LATEST POST
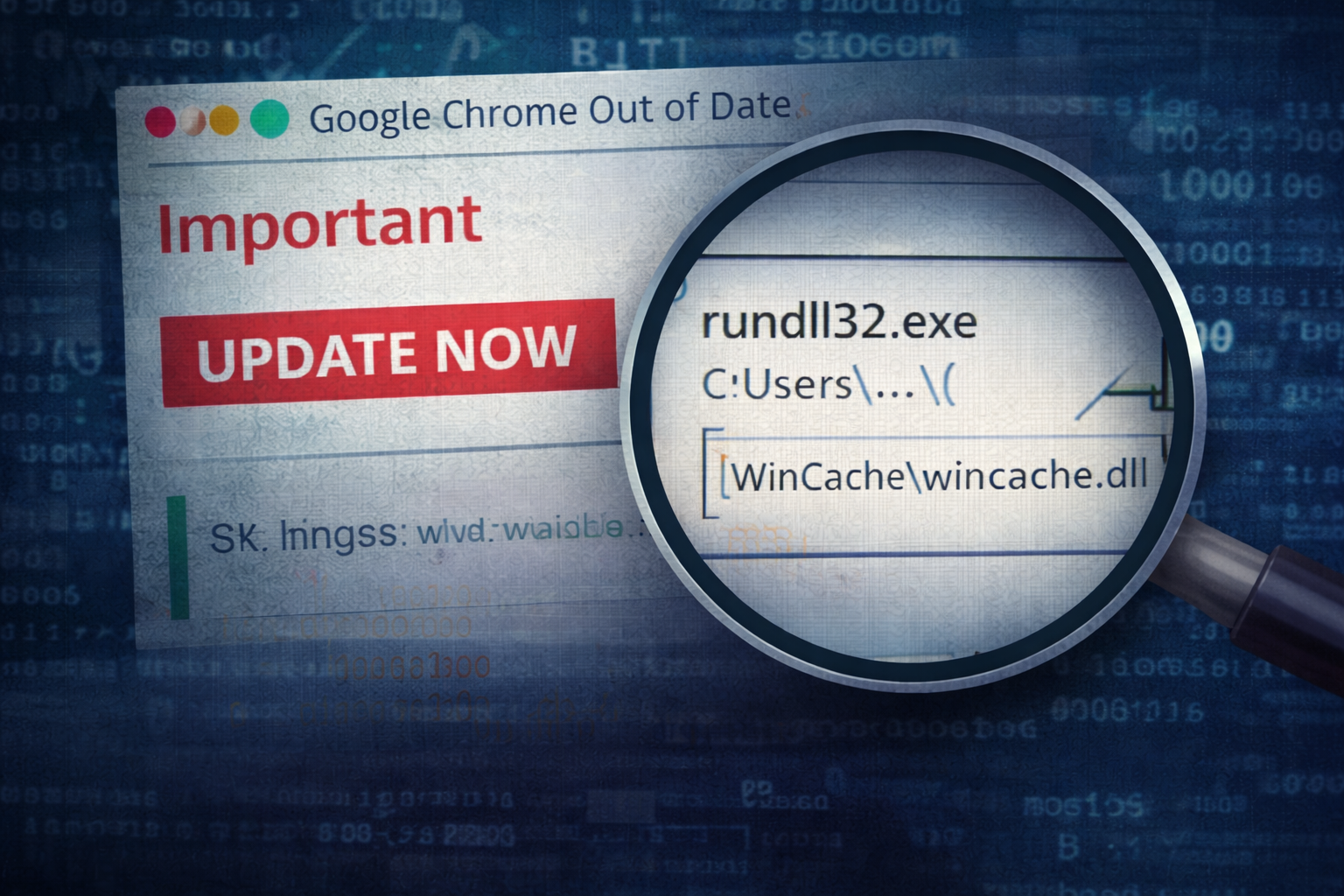
Fake Browser Update → Loader Execution in Minutes
A user clicks what looks like a routine browser update. Within minutes, a ‘legit’ installer chain pivots into rundll32 execution, persistence via scheduled tasks, and outbound beaconing to fresh infrastructure. This c...
FEATURED
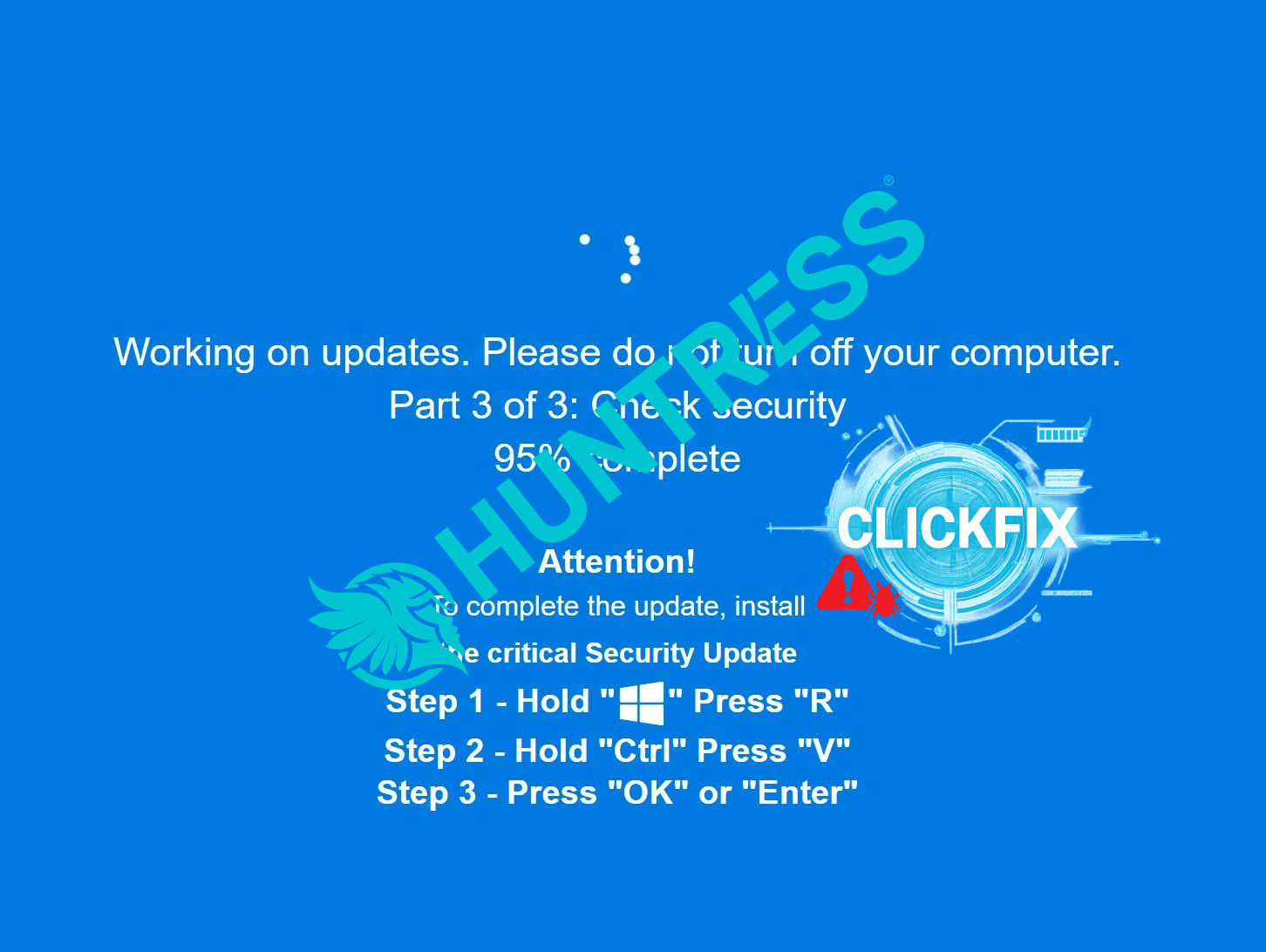
ClickFix Gets Sneaky: Lumma & Rhadamanthys Hiding in PNG Pixels
AI-Powered Malware: Dynamic Code Generation and the Rise of Adaptive Threats

AI Data Exposure — The Human Factor Behind GPT Incidents

Sextortion Scams Are Back: What They Are, How They Work, and Why They’re So Effective
PREVIOUS POSTS
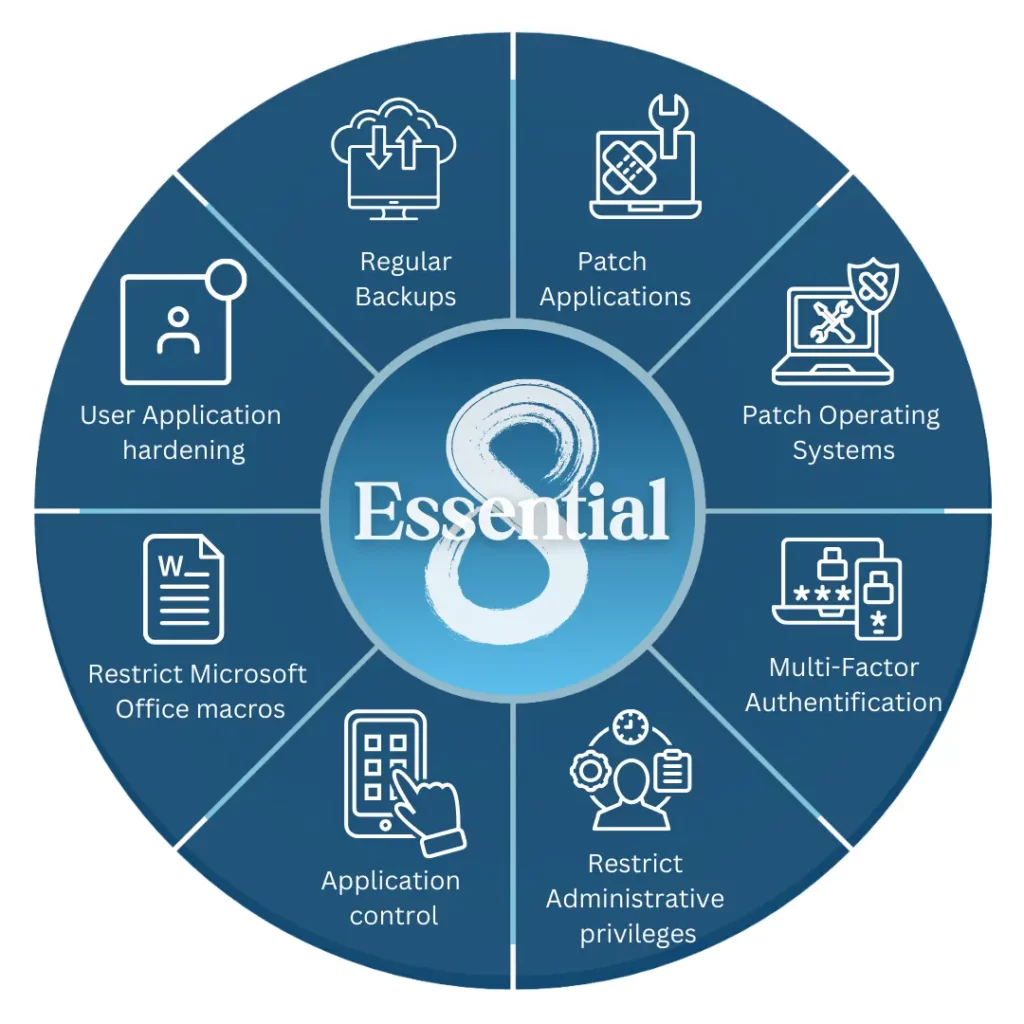
Implementing the ASD Essential Eight: Practical Hardening for Windows & Linux
The ASD Essential Eight is more than a checklist – it is a practical hardening baseline that can materially reduce the impact of real-world attacks. This guide walks through step-by-step implementation examples for ea...

Weekly Threat Trends — Week Commencing 5th January 2026
The first full week of 2026 is already shaping up around three themes: AI and identity converging into a single attack surface, data leaking through 'Shadow AI' and cloud abuse, and old-school ransomware and malware q...
Initial Access Brokers & Ransomware Chains
Commodity loaders and infostealers do not exist in a vacuum. They feed a market of Initial Access Brokers and ransomware affiliates who specialise in buying, packaging, and weaponising footholds into full-scale extort...

Weekly Threat Trends — Week Commencing 29th December 2025
This half-week at the end of 2025 and the first days of 2026 are a good moment to take stock: AI-driven intrusion chains, identity-led attacks, data extortion, and the growing role of DFIR all reshaped how defenders w...

Stealer-as-a-Service & the Credential Ecosystem
Infostealers are no longer just one-off binaries dropped by random phishing emails. They are part of a mature Stealer-as-a-Service ecosystem where logs are harvested, packaged, traded, and weaponised for everything fr...

Weekly Threat Trends — Week Commencing 22nd December 2025
With staff on leave, change freezes in place, and everyone distracted by end-of-year deadlines, threat actors use December to push BEC, gift-card fraud, shipping scams, and high-impact ransomware. This week’s post foc...

Evasive Loaders & Anti-Analysis Tricks in the Wild
Modern loaders decide if your environment is worth burning a payload on. This post unpacks how they fingerprint sandboxes, abuse LOLBins, and delay execution – and how to flip those anti-analysis tricks into reliable ...

Weekly Threat Trends — Week Commencing 15th December 2025
This week is all about trust abuse: poisoned package ecosystems, SSO and IdP missteps, remote management tooling turned into backdoors, and data extortion operations that never bother with encryption.

Memory Forensics for Stealers & Loaders
Stealers and loaders increasingly hide their most important behaviour in RAM. This post walks through how to follow the process tree, capture targeted memory dumps, and extract configs, C2s, and credentials so you can...





