LATEST POST

Weekly Threat Trends — Week Commencing 2nd March 2026
The first full week of autumn in Australia arrives with a very clear signal: attackers are leaning harder into enterprise edge and middleware, fake IT support is back in force, AI agents are becoming a real attack sur...
FEATURED

Remcos Goes Fileless (Again): Remote Templates, Equation Editor RCE, and .NET-in-Image Loading

Malware in the Subtitles: A Fake Movie Torrent That Assembles Agent Tesla via Layered PowerShell
ClickFix Gets Sneaky: Lumma & Rhadamanthys Hiding in PNG Pixels
AI-Powered Malware: Dynamic Code Generation and the Rise of Adaptive Threats
PREVIOUS POSTS

Weekly Threat Trends — Week Commencing 23rd February 2026
The final week of February rolls straight into the first day of autumn in Australia — and the threat landscape is matching the season shift: long-running data breaches are finally surfacing, ransomware campaigns are c...

Infrastructure Archaeology: What TLS Certificates Can Reveal
TLS certificates are more than encryption—they’re fingerprints. Even without packet capture, certificate metadata can help you map infrastructure, find sibling domains, identify staging patterns, and separate commodit...

From One Phish to Fleet-Wide Hunt: How I Expand Scope Safely
One phish is rarely one phish. The trick is expanding scope fast without detonating false positives, overwhelming teams, or blocking legitimate business traffic. This casefile-style post shows the exact pivots I use—f...

Weekly Threat Trends — Week Commencing 16th February 2026
The week of 16–22 February 2026 highlights how attackers are leaning hard on remote support tools, CRM platforms, national ID systems, fintech brokers and high-profile events as data sources — while hospitals, telecom...
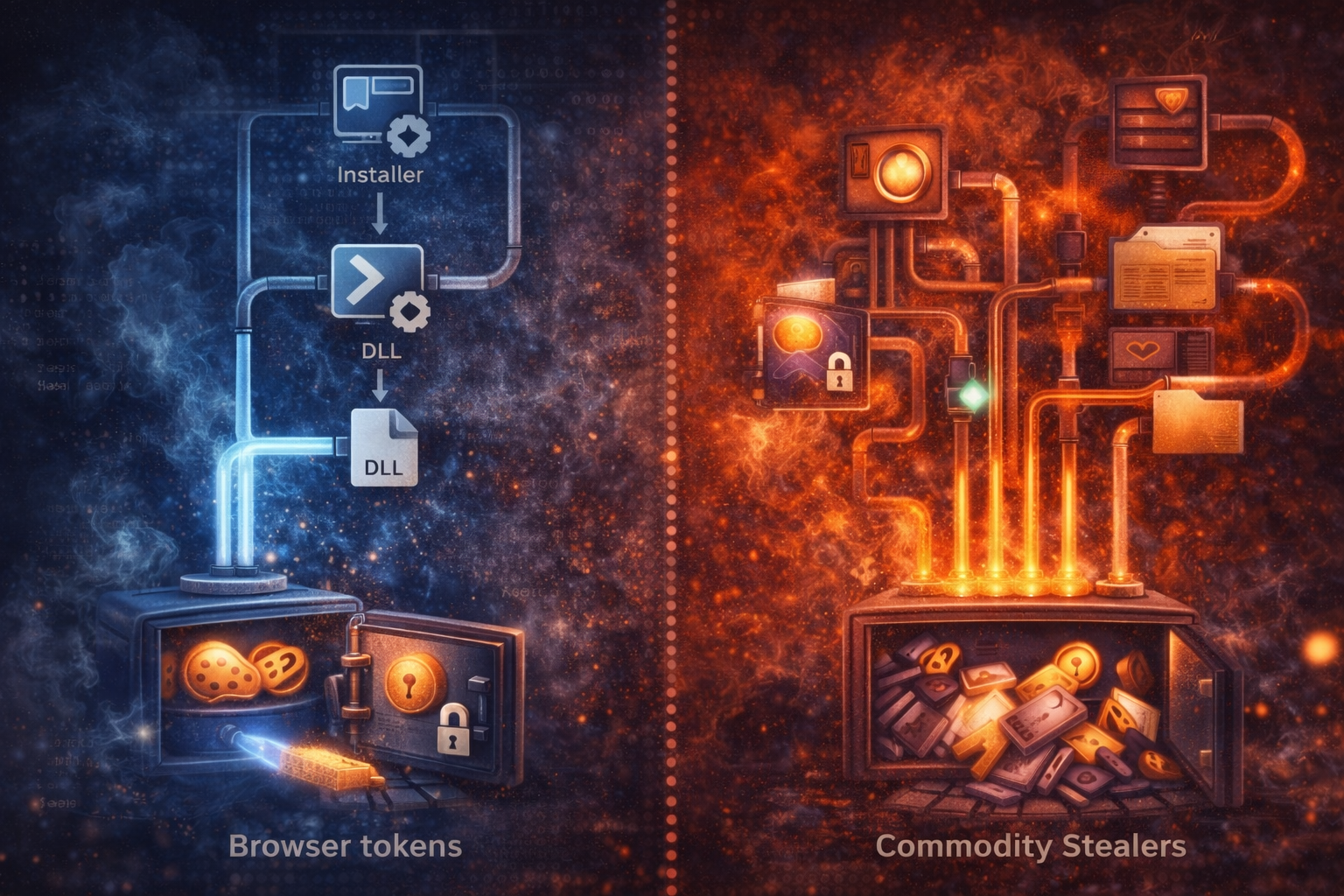
Family vs Family: Lumma vs Commodity Stealers (Artifacts That Give Them Away)
Stealers often look identical at first glance: browser DB access, cookie theft, rapid exfil, and a flood of IOCs. But there are consistent artifact-level differences that let you classify the intrusion fast—even witho...

Lab Notes: My “First 10 Minutes” Malware Triage Checklist (Written as a Story)
This is not a perfect-world DFIR process. It’s what I do in the first 10 minutes when an alert hits and the clock is ticking: capture the hinge artifacts, decide whether to contain, and set up pivots for scoping. Writ...

Weekly Threat Trends — Week Commencing 9th February 2026
The second week of February 2026 shows ransomware pivoting back to hard encryption, government and payment pipelines under pressure, unmanaged edge VMs being used as footholds, and consumer/IoT devices feeding some of...
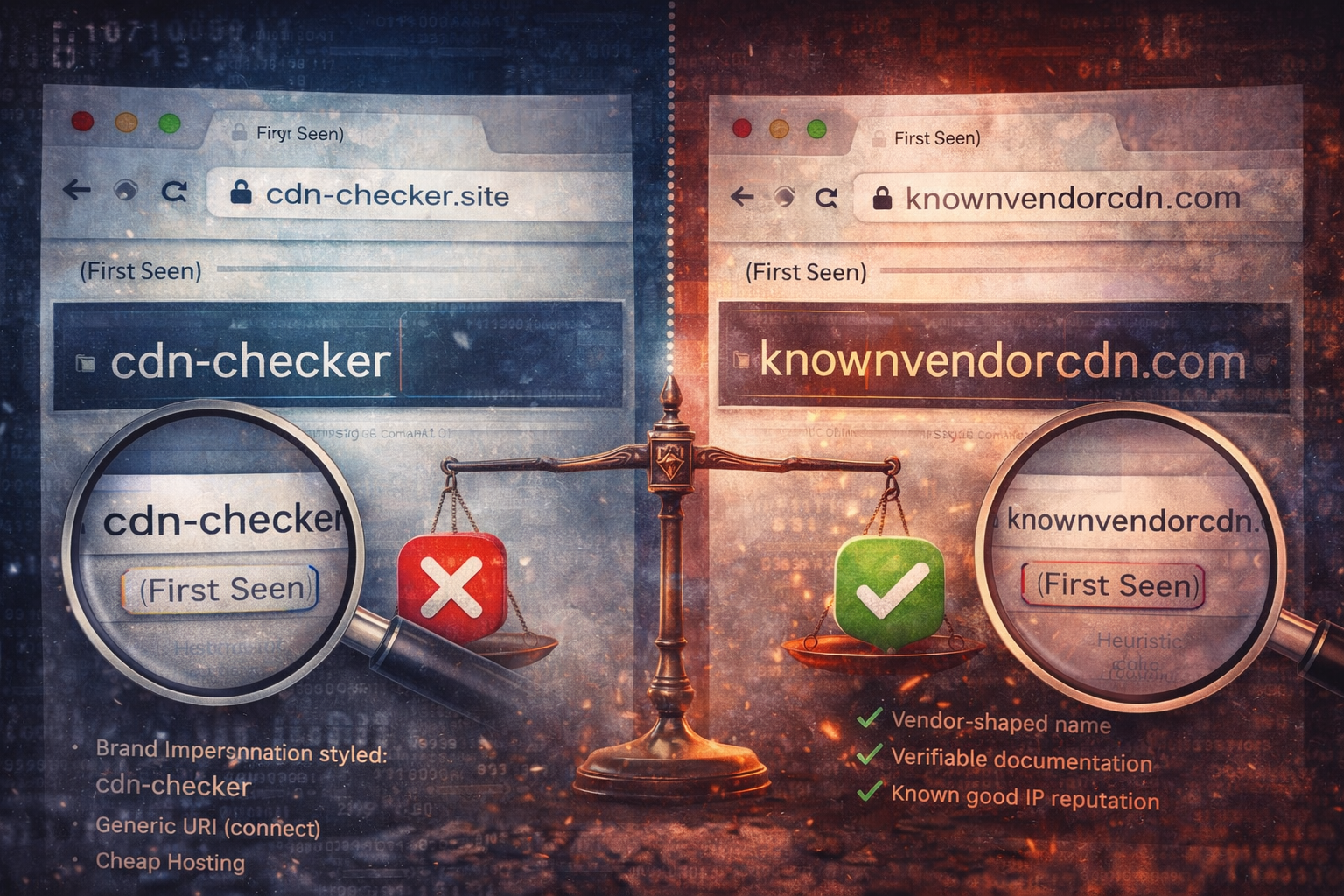
Myth: “New Domain = Malicious” (What Actually Matters)
A domain being ‘new’ to your environment is a weak signal on its own—sometimes useful, often misleading. This post breaks down why defenders overvalue ‘new domain’ alerts, what signals actually separate malicious infr...

Detection Diary: Catching Loaders With 3 Correlations
Loaders are built to blend in: a fake installer, a LOLBin hop, quiet persistence, then a clean HTTPS beacon. If you alert on single events, you drown. If you correlate three things, you catch the chain early. Here are...





