ClickFix Malware Campaign
How Fake Verifications Lead to Real Compromise
A new wave of attacks uses fake 'I'm not a robot' pages and clipboard tricks to make users infect themselves. Here's how it works, what it looks like, and how both users and security teams can respond.
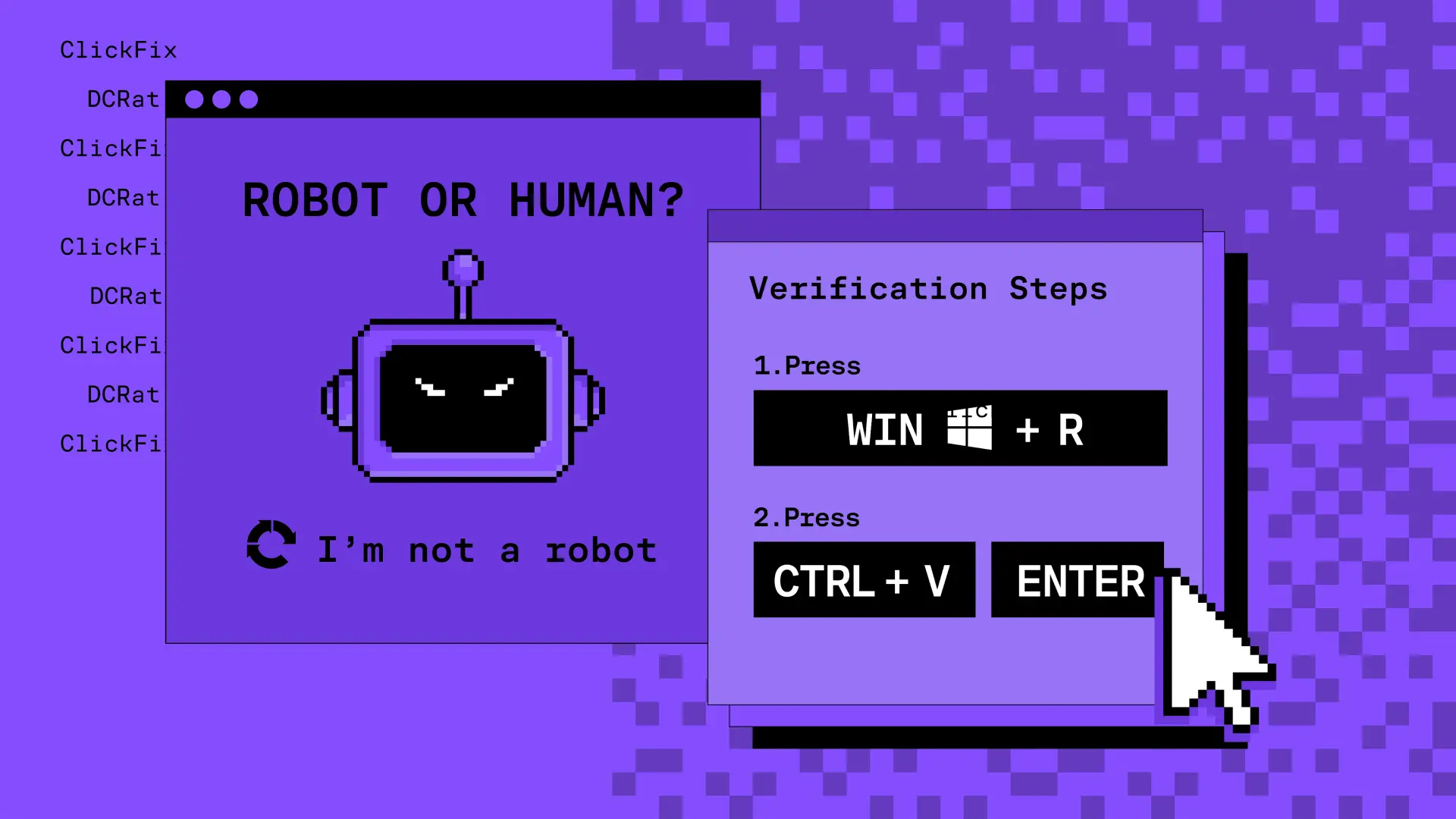
Sometimes the most dangerous code on your machine is the one you paste there yourself.

Introduction
It starts with a simple click. Maybe an ad for a free download, maybe a fake document link from someone you know. You’re taken to a site that looks normal enough — even has a padlock in the browser bar and a familiar domain ending in .co.uk or .net. A message pops up:
“Complete these verification steps to continue. Press Windows + R, paste the code, and press Enter.”
You think it’s a CAPTCHA check or some routine fix. But in reality, that “verification” just made you install malware — on your own device, by your own hand.
This is the new face of social engineering: the ClickFix campaign — a blend of phishing, malvertising, and clever clipboard manipulation designed to trick users into running malicious commands themselves.
In this post, we’ll break down how these attacks work, show what they look like, and explain what both security teams and everyday users can do to stop them.
The Attack Chain: From Lure to Takeover
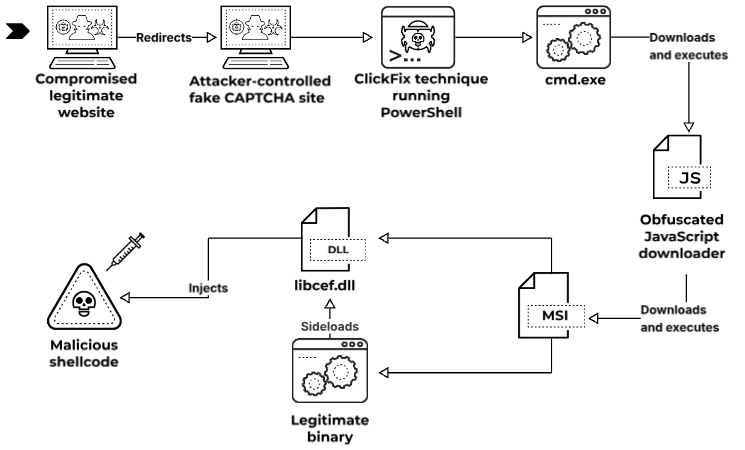
The ClickFix operation doesn’t rely on zero-days or sophisticated exploits. Instead, it manipulates human trust and routine computing habits.
Step 1. The Lure
Attackers distribute malicious links through:
- Emails posing as invoices, shipment updates, or document shares.
- Instant messages on Slack, Teams, or WhatsApp.
- Social media DMs from compromised accounts.
- Malvertising, where poisoned ads appear on Google or YouTube.
The goal is simple — get the user to click and land on the fake verification page.
Step 2. The ClickFix Page
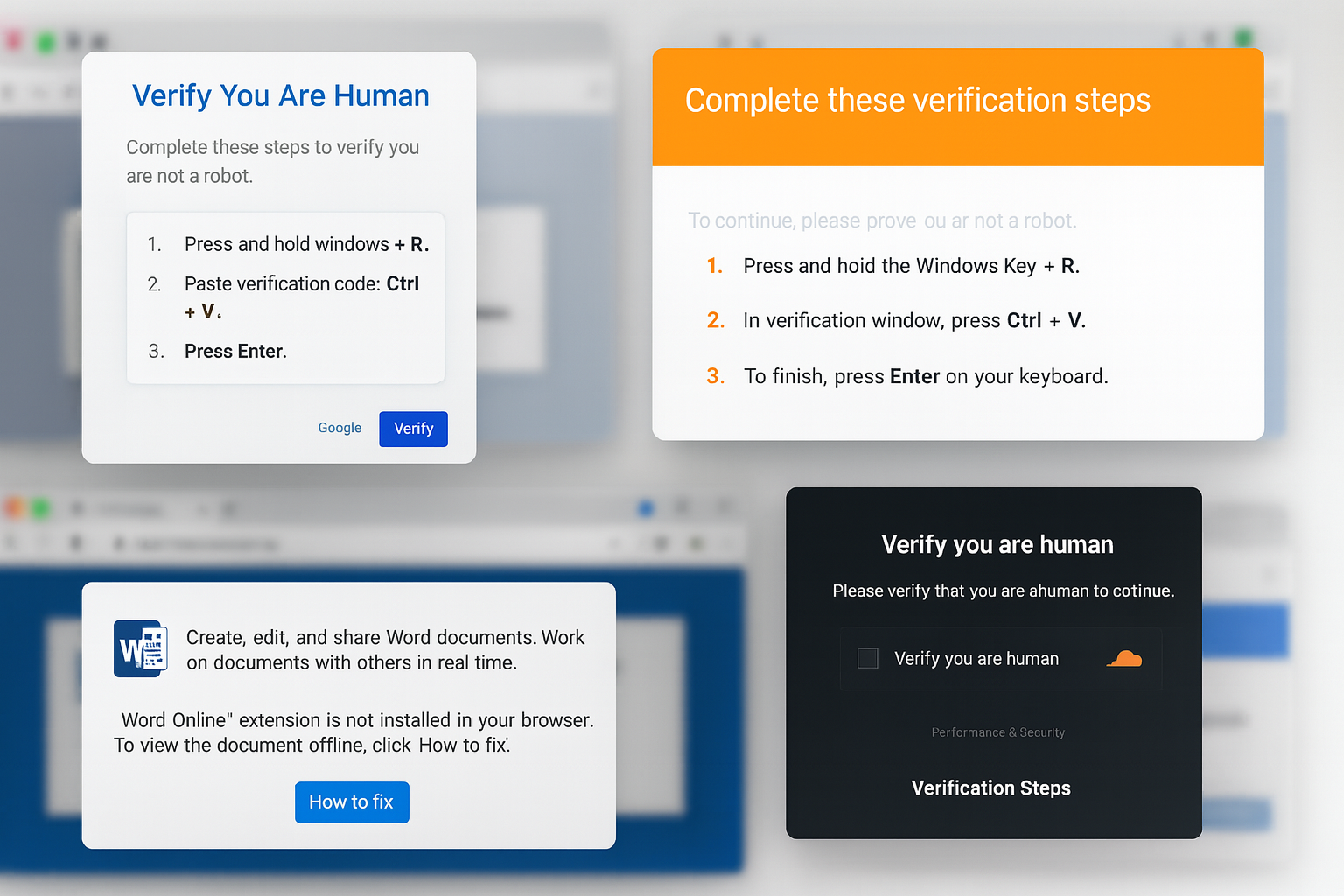
Once the user clicks the lure, they’re redirected to a realistic-looking page that mimics a CAPTCHA, browser verification, or even a “Word Online” installation notice. The text usually reads:
“To verify you are not a robot, press Windows + R, then press Ctrl + V, and Enter.”
Behind the scenes, the site copies a malicious PowerShell or script command to the clipboard — waiting for the user to paste and execute it. This is the heart of the ClickFix trick: the user delivers the payload for the attacker.
Step 3. Code Execution
The moment the copied code is executed, the attacker gains control. The script typically:
- Downloads an executable or loader from a remote server.
- Installs a stealer (like Raccoon or Vidar) or remote access tool.
- Establishes persistence on the host.
From that point, data exfiltration begins — credentials, cookies, browser sessions, crypto wallets, or anything stored locally.
Step 4. Credential and Cookie Theft
The stolen information is immediately used to access cloud apps, corporate email, and MFA-protected accounts via stolen session cookies. This method allows attackers to bypass authentication entirely — no passwords or OTPs required.
Step 5. Account Takeover
Attackers then move laterally within the compromised environment, taking over business apps and data. For organizations, one careless click can cascade into a full account compromise, cloud infiltration, or ransomware deployment.
Why It Works So Well
- The illusion of legitimacy — pages often mimic Google, Cloudflare, or Microsoft verification steps, complete with branding and SSL certificates.
- User familiarity — pressing Win + R feels routine for anyone who’s followed IT instructions before.
- Lack of technical red flags — no downloads, no attachments, no obvious phishing form — so most security filters don’t trigger.
- Clipboard abuse — modern browsers’ Clipboard API makes it trivial for sites to automatically copy malicious commands without user awareness.
A line of JavaScript is all it takes:
async function copyToClipboardModern(command) {
await navigator.clipboard.writeText(command);
}
Combine that with a “Verification in progress…” spinner and users will trust the process. The psychology does the rest.
Real-World Examples
Attackers often host these fake pages on compromised legitimate sites, giving them built-in credibility. For example:
- A garden equipment site like
https://bladesgardenmachinery.co.ukmight be hacked and used to deliver a “Verify you are human” popup. - Other variants impersonate Microsoft Office or Google Drive, asking users to “Enable Online Editing” or “Install Word Extension.”
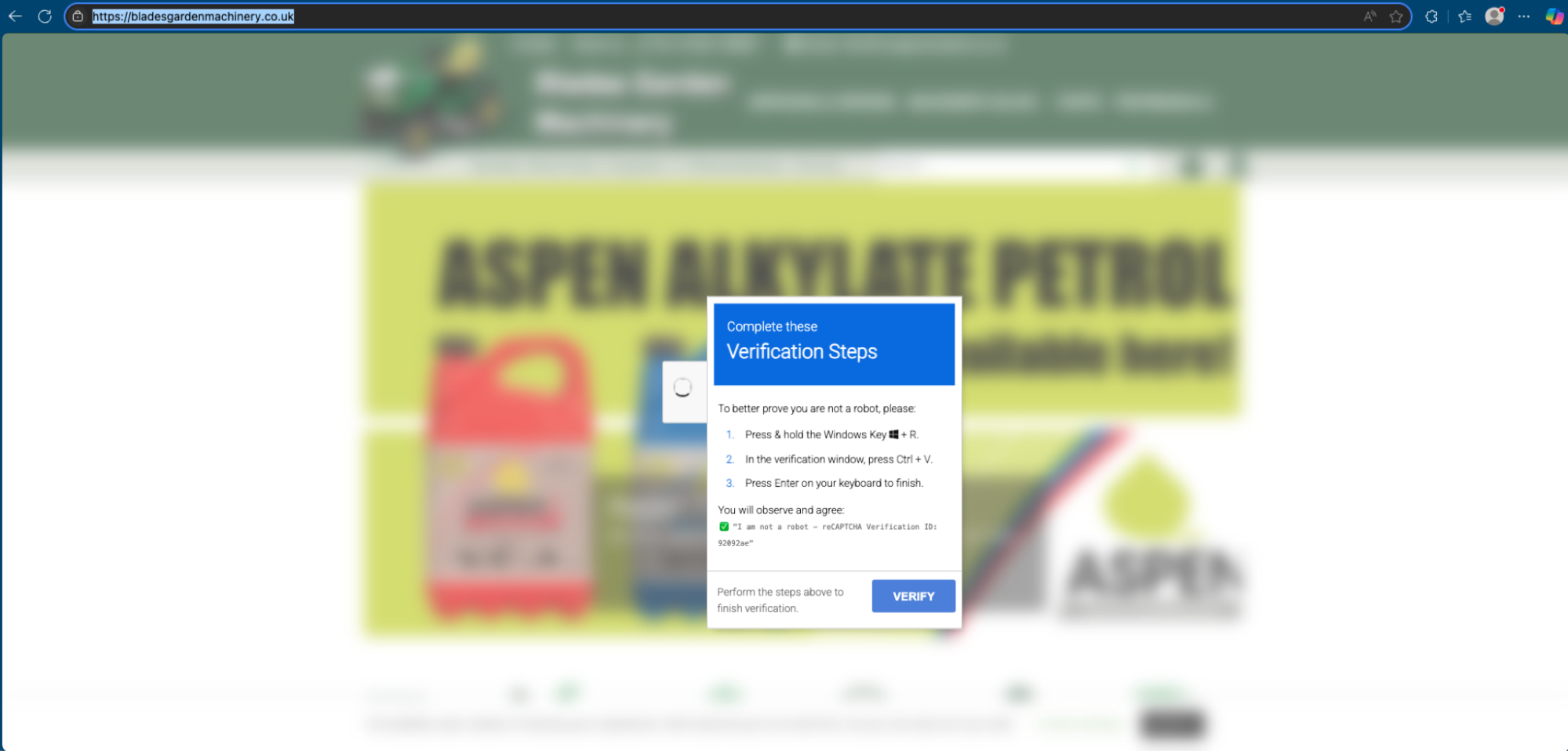
Each of these pages ultimately directs victims to execute a malicious command copied from the clipboard. The prompt varies, but the pattern is the same: do something technical that feels routine but actually installs malware.
Technical Breakdown: The Clipboard Trap
Here’s what the modern JavaScript on these pages does:
- Copies command silently — using the Clipboard API to store a pre-built PowerShell or cmd command.
- Shows verification progress — a fake loading spinner appears while the user follows the steps.
- Prompts manual execution — the site instructs the user to open Windows Run (Win + R), paste, and press Enter.
- Executes remote payload — typically via a PowerShell one-liner fetching a malicious executable.
The code snippet might look harmless but hides malicious intent. In some cases, attackers use base64-encoded payloads or obfuscation to evade detection.
Once executed, the script can:
- Disable antivirus temporarily.
- Create persistence (scheduled task or registry entry).
- Inject into browser processes to grab tokens and cookies.
What Users Should Do (and Never Do)
If You See a “Verification Steps” Page
- Do not follow any instructions that involve pressing Win + R, Ctrl + V, or Enter.
- Do not copy and paste any commands from the web into your system tools.
- Close the page immediately.
- Run an antivirus or endpoint scan.
- Report the site to your IT or security contact.
If You Already Ran the Command
- Disconnect from the internet immediately. This stops further data exfiltration.
- Do not reboot yet. Security teams may need to analyze volatile data.
- Inform IT or security staff right away. Provide the URL, time, and a screenshot if possible.
- Run a full offline scan using your security software.
- Change passwords from a clean device. Focus on email, banking, and work accounts.
Don’t Feel Embarrassed
These attacks are designed to look convincing. Even experienced users have fallen for them. The key is to report quickly — silence gives the attacker more time to act.
Guidance for Security Teams
ClickFix-style attacks require a mix of user training, technical controls, and hunting.
1. Block and Monitor
- Add known domains to your web proxy and DNS blocklists.
- Deploy web content filters capable of identifying clipboard access attempts.
- Use browser isolation for high-risk categories (ads, social, unknown referrers).
2. Detect Suspicious Behavior
- Look for PowerShell or cmd invocations from explorer.exe or chrome.exe.
- Set up alerts for command-line arguments like
-EncodedCommandor URLs in PowerShell commands. - Review clipboard access logs if your EDR supports them.
3. Containment and Response
- Quarantine affected endpoints.
- Dump network traffic for outgoing connections to identify C2 addresses.
- Rotate credentials for affected users and disable active sessions.
- Block IPs and domains associated with the campaign.
4. Awareness and Simulation
- Run phishing simulations including clipboard‑based lures.
- Teach users that legitimate IT requests never ask for Win + R commands.
Why Traditional Defenses Struggle
Security tools are tuned to catch downloads, attachments, and known malicious links. ClickFix bypasses those by:
- Avoiding direct file delivery.
- Using legitimate scripting tools built into Windows.
- Relying entirely on user interaction.
It’s a social-engineering exploit, not a software exploit — and that’s why it works so consistently.
Recovery and Hardening
For both individuals and organizations, recovery steps include:
- Reimage or clean infected systems. If infection is confirmed, don’t trust the machine until it’s rebuilt.
- Enable MFA everywhere. Even if cookies were stolen, app-based MFA adds friction.
- Clear browser cookies and sessions. Attackers love reusing session tokens.
- Update browsers and extensions. Many clipboard-related security improvements rely on current versions.
- Use endpoint protection with behavioral analysis. Signature-based AV alone won’t catch this.
The Bigger Picture
ClickFix is just one flavor of a larger trend — attackers no longer rely on technical exploits when human behavior is easier to manipulate. They hijack trust, routine, and even legitimate web features to get what they want.
Phishing used to be about stolen passwords. Now it’s about socially engineered execution — convincing users to run the payload themselves.
Key Takeaways
- Fake verification pages are not harmless; they’re attack vectors.
- Never run commands from websites or messages — no matter how official they look.
- Security teams should monitor clipboard and PowerShell behavior closely.
- Education remains the strongest defense.
Attackers don’t need exploits when users will paste the payload for them. Awareness and swift reporting are the new firewalls.


