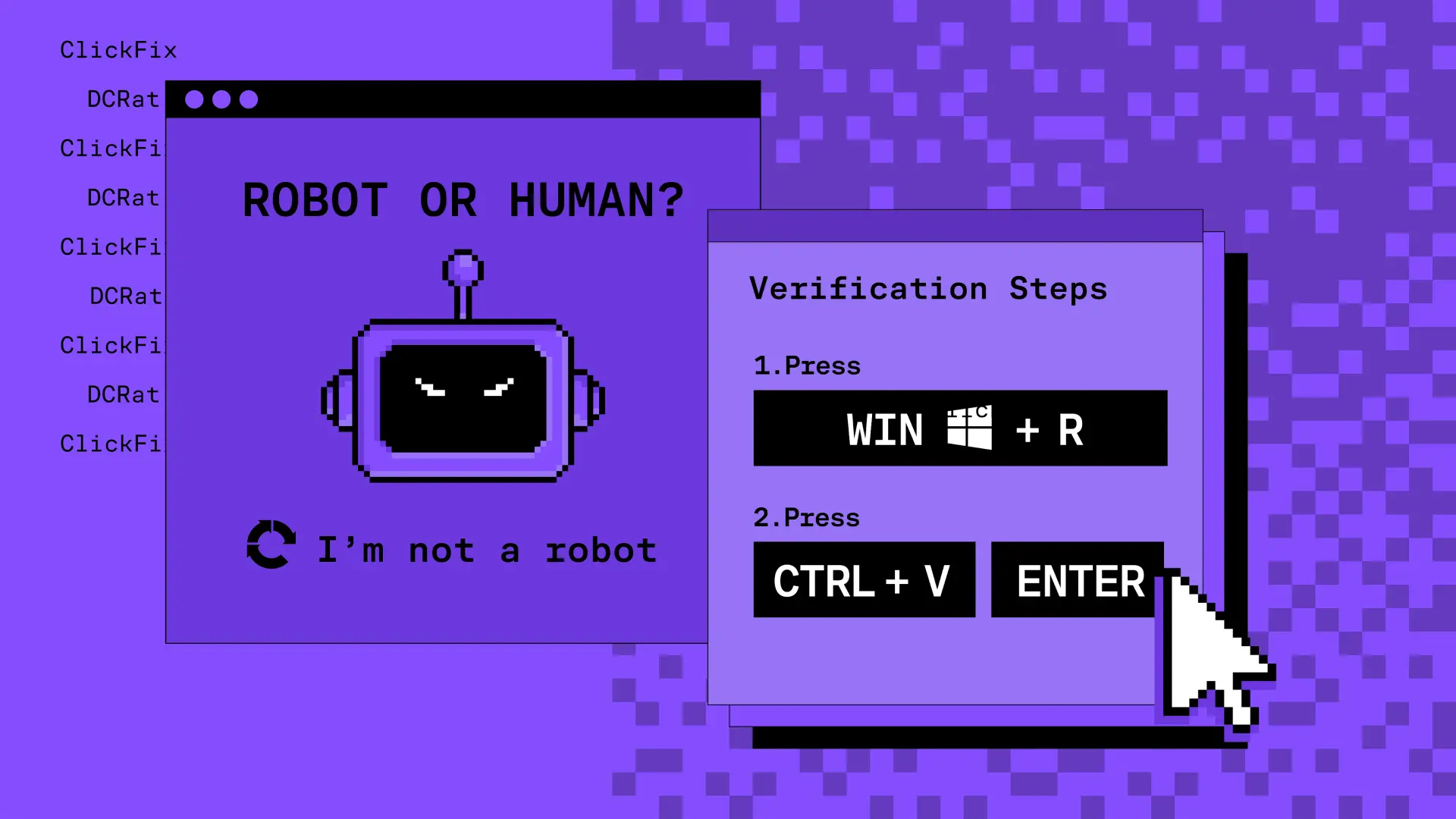
Incident Response 101 (Part 1)
What to Do If You Click a Bad Link
Everyone slips up eventually — even professionals. This guide walks you through exactly what to do in the crucial first minutes after clicking a malicious link.But what matters most isn’t the click — it’s what you do *next.* This article breaks down the **critical first minutes and hours** after clicking a suspicious link or opening a malicious attachment, explaining the right steps to take, what not to do, and how to recover without panic.

The difference between a small scare and a full-blown breach isn’t luck — it’s how fast and smartly you respond.

Introduction
We all make mistakes. Even cybersecurity experts sometimes click before they think — curiosity, fatigue, or habit taking over in a split second. In phishing and social engineering attacks, that moment is what the attacker counts on.
But what matters most isn’t the click — it’s what you do next.
This article breaks down the critical first minutes and hours after clicking a suspicious link or opening a malicious attachment, explaining the right steps to take, what not to do, and how to recover without panic.
Step 1: Don’t Panic — Disconnect and Assess
The first reaction most people have is panic — which leads to poor decisions. Take a deep breath and act methodically.
1. Disconnect from the Network
Immediately turn off Wi‑Fi or unplug the Ethernet cable. If you’re on mobile, disable data. This prevents further communication between the potential malware and its command server.
2. Leave the Tab or App Open
Resist the urge to close everything instantly — forensic teams may need the browser history, page source, or URL for later analysis. Instead, take a screenshot of what you clicked, including the address bar.
3. Make a Quick Note
Write down the time, device name, and what exactly you did (e.g., “Clicked a link in invoice.pdf at 10:42 AM”). These details become crucial in incident reports.
Step 2: Report — Don’t Try to Fix It Alone
Many people hesitate to report incidents out of fear of embarrassment or blame. In reality, silence causes more damage than the click itself.
Why Reporting Early Matters
- Security teams can isolate systems, block malicious domains, and prevent wider compromise.
- If credentials were entered, they can force password resets enterprise‑wide.
- Quick reporting helps identify trends — one employee’s mistake might be the first sign of a targeted campaign.
What to Include When Reporting
- Time and nature of the click
- Screenshot or copied link
- Whether credentials were entered or files downloaded
- System used (work laptop, personal mobile, etc.)
If you’re not sure whom to contact, report it to your IT Helpdesk or Security mailbox — most organizations have one (like security@yourcompany.com).
Step 3: Contain — Stop the Spread
If malware or credential theft is suspected, containment becomes priority.
1. Run an Offline Malware Scan
Use your endpoint security tool in offline or safe mode. Disconnect before scanning so malicious code can’t call home.
2. Change Passwords — But Carefully
Only change passwords from a clean device. If your work computer might be compromised, use another trusted system.
3. Check for Unusual Account Activity
Review recent logins, sent emails, and MFA prompts. Attackers often pivot fast once they gain access.
4. Revoke Active Sessions
Log out of all sessions from your email provider, cloud accounts, or social networks. This cuts off any attacker still connected.
Step 4: Investigate — Know What You’re Dealing With
Your IT or security team may conduct forensic analysis to understand what the link did. Even for individuals, tools like VirusTotal or URLScan.io can safely check URLs.
How to Analyze a Suspicious Link (Safely)
- Copy the URL (don’t click).
- Visit VirusTotal.com and paste the link.
- Look for detection results from multiple antivirus engines.
- Take note of IP addresses, redirect chains, or downloaded payloads.
This gives context: was it credential phishing, malware delivery, or just ad spam?
Step 5: Recover and Strengthen Defenses
1. Reset Passwords and Enable MFA
Even if you didn’t enter credentials, rotate them. MFA (especially via app, not SMS) stops most credential reuse attacks.
2. Clear Saved Logins and Cache
Remove autofill credentials and cookies — these are often targeted for session hijacking.
3. Backup and Patch
If infection is confirmed, back up critical files before reinstalling or re‑imaging the system. Then patch everything: browser, OS, extensions, plugins.
4. Inform Others
If the link came via email, text, or collaboration tools, warn others not to interact with it.
Why This Happens — and Why It’s Not Always Your Fault
Phishing attacks work because they target emotion, not intelligence. Urgency, authority, curiosity — they all exploit human psychology. Even trained professionals occasionally fall for convincing lures, especially those crafted with AI or deepfake impersonations.
The key isn’t perfection — it’s preparation. The faster your response, the less power the attacker retains.
Key Takeaways
- Disconnect immediately, don’t panic.
- Report the incident — silence causes greater damage.
- Only change passwords from a trusted device.
- Scan offline, document everything.
- Mistakes happen — swift response prevents escalation.
Cyber resilience begins the moment you stop hiding mistakes and start managing them intelligently.