Salesforce Abuse in Meta Support Phishing
How Threat Actors Exploit Trusted Platforms
Threat actors are leveraging Salesforce’s trusted infrastructure to deliver phishing campaigns impersonating Meta Support. Discover how these scams work, why they’re effective, and how to protect your business accounts.

Threat actors are abusing Salesforce’s trusted infrastructure to deliver convincing phishing campaigns that impersonate Meta’s Business Support team. This emerging trend highlights how legitimate SaaS ecosystems can be weaponized to bypass enterprise defenses and target digital marketers, ad managers, and corporate users worldwide.
Introduction
A new phishing wave has been observed abusing Salesforce’s Marketing Cloud infrastructure to impersonate Meta Business Support.
The emails, which appear professional and credible, claim that the recipient’s Meta Ad Account has been temporarily restricted due to advertising policy violations.
This campaign demonstrates a dangerous evolution in phishing tactics — attackers no longer rely solely on compromised web servers, but instead leverage legitimate enterprise tools like Salesforce to host and distribute their malicious redirects.
Anatomy of the Phishing Email
The lure arrives as a seemingly authentic support notification:
Subject: Temporary changes to your ad account – [Ticket ID: FBC7832HS721]
From: Juan Ch. jchavezmagana@salesforce.com
Sent via: Salesforce Marketing Cloud (e360.salesforce.com)
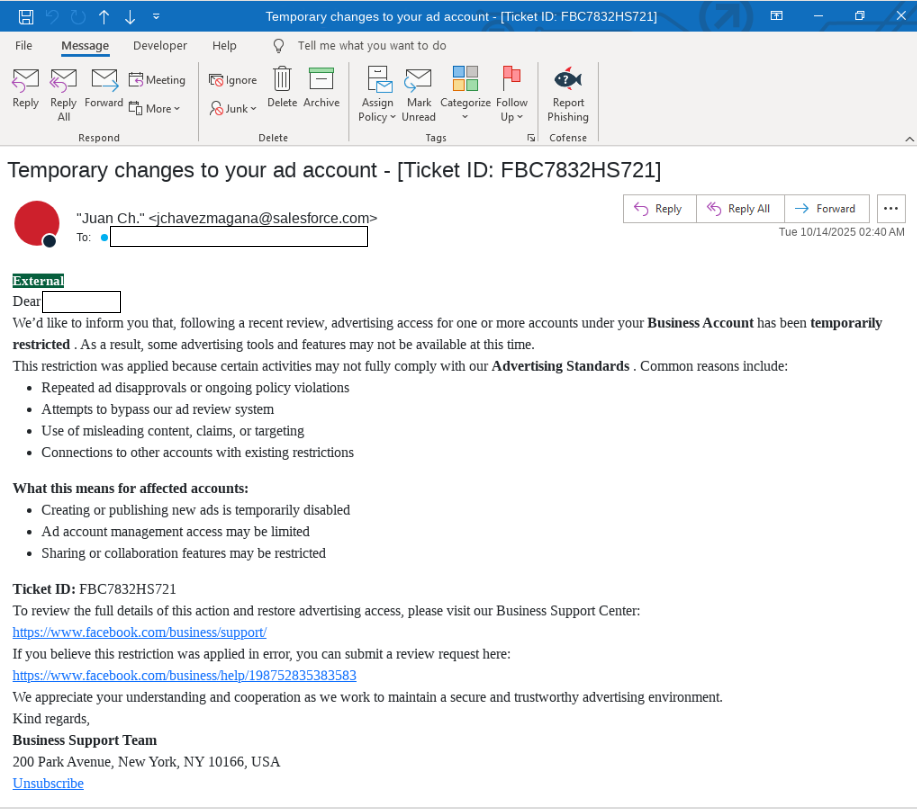
The message warns the user that their business ad account has been “temporarily restricted” and lists possible reasons, such as:
- Repeated ad disapprovals or ongoing policy violations
- Use of misleading content or targeting
- Links to restricted accounts
It then urges the recipient to review the restriction via the embedded “Business Support Center” link — visually a Facebook URL, but underneath, a Salesforce tracking redirect.
Abusing Trusted Salesforce Infrastructure
The embedded links follow patterns such as:
https://8tgtt5[.]2.tracking[.]e360.salesforce[.]com/click?jwf=eyJ0eXAiOiJKV1Qi...
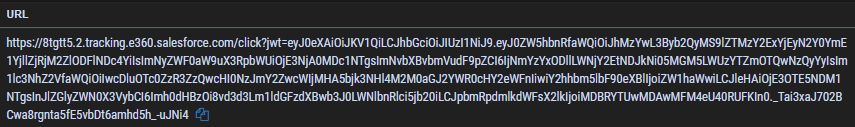
These are genuine Salesforce-hosted tracking URLs — part of the company’s marketing automation framework — but in this case, hijacked to deliver a malicious redirect.
This technique offers attackers multiple advantages:
- Domain Trust –
salesforce.comis globally whitelisted by most email gateways. - SSL Certificate Validity – Ensures HTTPS padlock legitimacy.
- Tracking Redirects – Allow seamless concealment of the true destination.
- High Deliverability – Emails from Salesforce infrastructure often evade spam filters.
In short, attackers weaponize Salesforce’s own trust and deliver phishing traffic under the guise of legitimate customer communications.
The Fake Meta Support Portal
Clicking the Salesforce link redirects victims to a spoofed Meta Support portal hosted on a fraudulent domain:
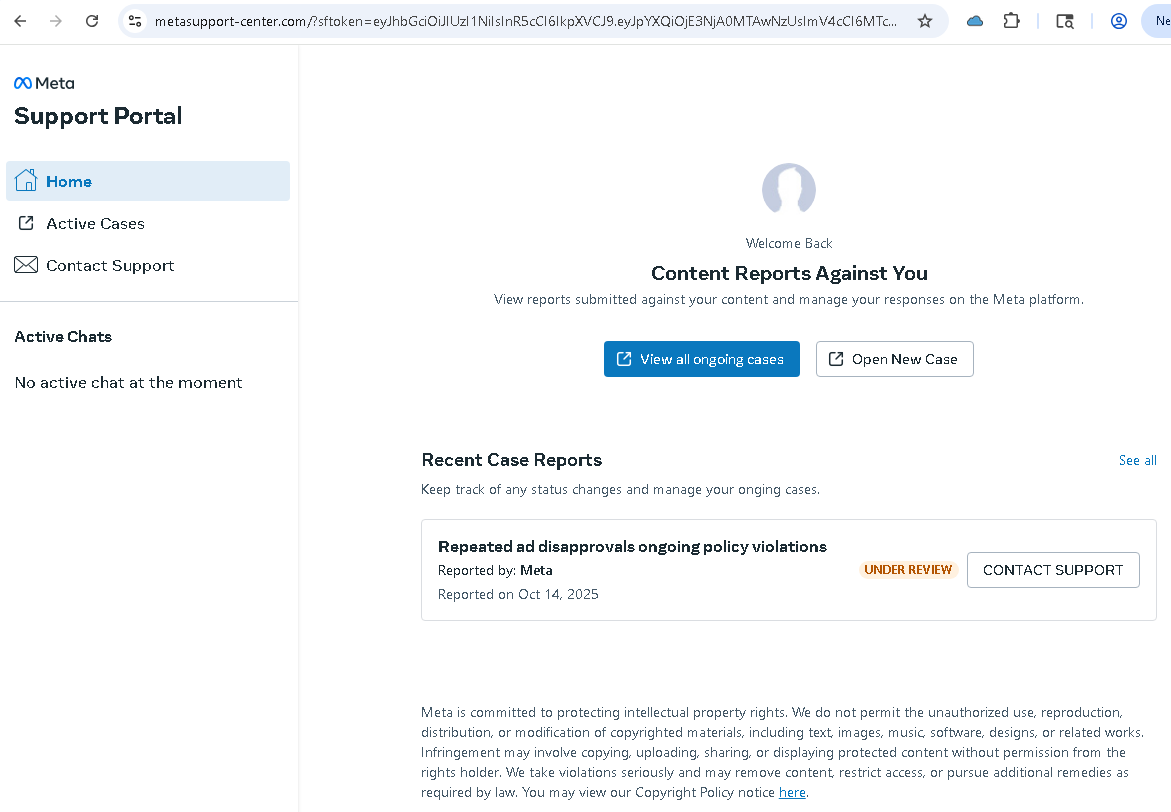
The site is a near-perfect clone of Meta’s real business help interface, including:
- A “Content Reports Against You” dashboard
- Fake case IDs (e.g., FBC7832HS721)
- Buttons for “View all ongoing cases” and “Open New Case”
- Meta logos, typography, and tone matching the genuine support environment
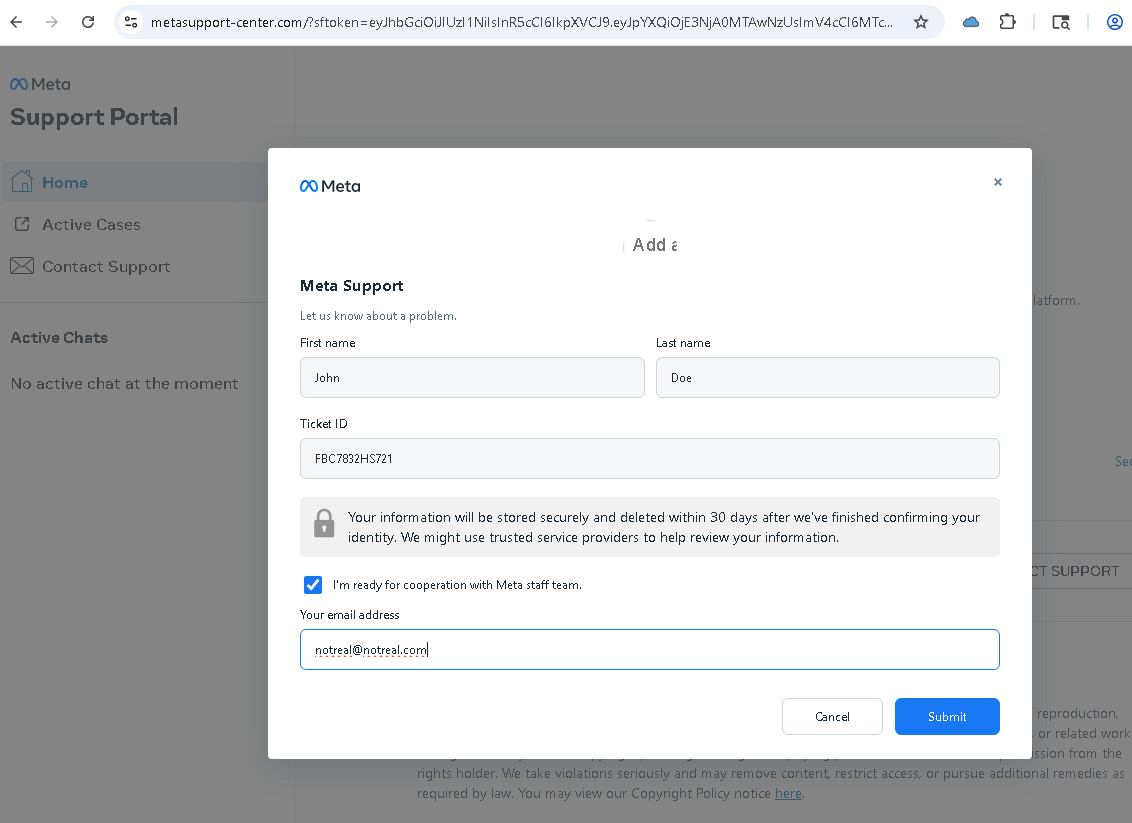
Once the victim selects “Contact Support,” a modal appears requesting their name, business email, and confirmation checkbox.
This data is silently exfiltrated to an attacker-controlled backend.
Technical Breakdown
Observed Redirect Chain
| Stage | Domain | Description |
|---|---|---|
| 1 | salesforce.com |
Abused legitimate tracking domain |
| 2 | metasupport-center[.]com |
Fake Meta portal for data collection |
| 3 | [hidden backend endpoint] | Captures submitted credentials |
Example Email Structure
- Display Name: Juan Ch.
- Envelope Domain: salesforce.com
- Reply-To: Empty or mismatched
- Message-ID: Salesforce Marketing Cloud format
- URLs: Redirect via
e360[.]salesforce.com
The Psychological Hook
The content leverages authority and urgency, two of the strongest social engineering triggers:
- Authority: Uses official Meta branding, ticket numbers, and corporate tone.
- Urgency: Threatens advertising suspension and limited access.
- Familiarity: Meta advertisers often deal with legitimate policy reviews, making the scenario believable.
This perfect storm of trust signals makes the email remarkably effective at bypassing human suspicion.
Why Salesforce Is a Prime Target
Salesforce Marketing Cloud enables organizations to send large volumes of legitimate customer communications. However, when an account is compromised or misused, its reach and reputation amplify the impact of phishing.
Key reasons attackers exploit it:
- Trusted Domains – Rarely flagged by filters.
- Scalable Email Infrastructure – Can send high volumes efficiently.
- Built-in Redirection – Perfect for concealing phishing endpoints.
- Complex Tenant Ownership – Makes abuse difficult to attribute or remediate quickly.
This represents a growing class of threat known as “SaaS abuse phishing.” Attackers no longer host malicious payloads on sketchy servers — they weaponize legitimate SaaS ecosystems.
Real-World Implications for Victims
For digital marketing teams and small businesses, the fallout can be severe:
- Credential Theft: Business account login data harvested.
- Ad Account Hijacking: Attackers run fraudulent ads using stolen funds.
- Brand Reputation Damage: Compromised accounts distribute scams or malware.
- Recovery Delays: Meta account restoration can take weeks, disrupting campaigns and analytics.
In one captured session, the fake portal’s form data submitted “John Doe / notreal@notreal.com” — confirming the page’s data capture function works regardless of input validity.
Indicators of Compromise (IOCs)
Domains and URLs:
https://8tgtt5[.]2.tracking[.]e360.salesforce[.]com/click?jwf=...
https://metasupport-center[.]com/?fstoken=...
Email Subject:
Temporary changes to your ad account – [Ticket ID: FBC7832HS721]
Spoofed Sender:
Juan Ch. <jchavezmagana@salesforce.com>
Observed Host:
metasupport-center[.]com (registered October 2025)
Detection and Mitigation
-
Hover Before Clicking
Verify URLs by hovering over them — if the visible text differs from the actual link, treat it as suspicious. -
Authenticate Directly
Access Meta Business Support only through: https://business.facebook.com/business/help -
Report Abuse
Salesforce users should forward such emails to:
abuse@salesforce.com
Meta-related phishing can be reported via:
phish@fb.com -
Enforce MFA
Enable multi-factor authentication on all Meta Business accounts. -
Educate Marketing Teams
Run awareness sessions focusing on SaaS-based phishing tactics.
Lessons from This Campaign
This phishing wave showcases a refined attack chain built on legitimacy, trust, and automation:
- Trusted SaaS (Salesforce) abused for redirection.
- Recognizable brand (Meta) impersonated for credibility.
- Professional UI (fake portal) used for harvesting.
It’s a stark reminder that security by reputation is no longer reliable. Even the world’s most trusted enterprise platforms can become tools of deception when compromised or misused.
The Bigger Picture
As organizations move their marketing and communication pipelines into the cloud, attackers follow.
The Salesforce–Meta phish highlights how threat actors adapt to digital ecosystems faster than traditional defenses can respond.
Defending against this new generation of phishing requires visibility across SaaS services, adaptive threat intelligence, and continuous employee education.
Key Takeaways
- Salesforce infrastructure is being abused to deliver Meta phishing campaigns.
- Legitimate SaaS trust can be exploited to bypass filters and fool users.
- Attackers rely on visual precision and business familiarity rather than malware.
- Verification through official dashboards is the safest path.
- Awareness training is still the most cost-effective defense.
Phishing no longer hides behind shady links — it now lives within trusted clouds. Recognizing the abuse of legitimate platforms like Salesforce is essential to protecting your organization from the next generation of brand impersonation attacks.


