Scam Awareness
[A Complete Guide]
From fake renewals to crypto giveaways, tech support calls, parcel texts, and romance investment schemes, this post centralizes the most high-impact scams you need to know about, with real-world examples and red flags to spot.

Scams are no longer simple email tricks, they are multi-layered social engineering attacks designed to exploit urgency, trust, and emotion. In this consolidated guide, we’ll explore the most prevalent scams targeting everyday users and staff in 2025. Each section is presented in full detail, exactly as you’d encounter them in practice, including red flags, examples, and step-by-step defense tips.
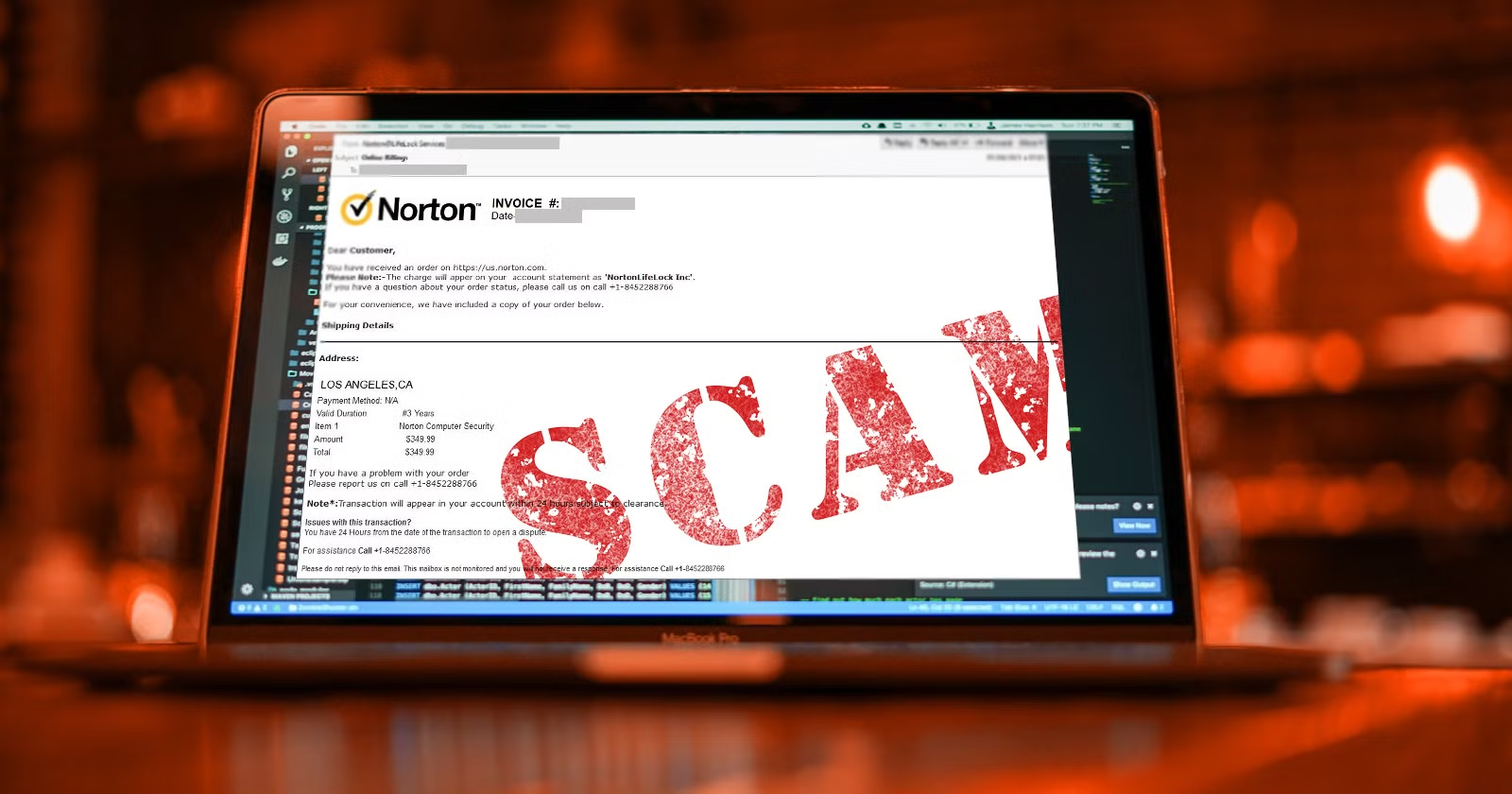
Subscription Renewal Scams — “Your Norton Is Expiring”
Subscription renewal scams exploit fear and urgency by sending fake antivirus or software renewal notices, often targeting non-technical users like seniors or small business owners. These scams arrive via emails, browser popups, text messages, or even phone calls impersonating trusted brands like Norton, McAfee, or Microsoft. In 2024, the Federal Trade Commission (FTC) reported over $200 million in losses to tech support and subscription scams, with a 30% increase in cases targeting users over 60.
How the Scam Works
Scammers craft convincing messages to trick users into believing their software subscription (e.g., antivirus, cloud storage, or streaming services) has expired or auto-renewed. A typical email might look like:
Subject: URGENT: Your Norton 360 Deluxe Subscription Has Expired
Body: Your subscription expired on July 10, 2025. To avoid losing protection against viruses and malware, call our support team at 1-800-555-1234 or click here to update your payment details. Failure to renew may result in data loss.
Once you engage by calling, clicking a link, or responding the attacker, posing as a customer service representative, may:
- Request remote access to your device using tools like TeamViewer or AnyDesk, claiming they need to “fix” your subscription.
- Ask for payment details (credit card or bank info) to “process a renewal” or “issue a refund.”
- Install malware, such as keyloggers or ransomware, in the background while pretending to troubleshoot.
- Trick you into logging into your bank account under the guise of verifying a refund, allowing them to steal credentials or transfer funds.
- Use social engineering to extract sensitive information, like your Social Security number, by claiming it’s needed for “account verification.”
Common Variants
Scammers adapt their tactics to different platforms and brands. Here are the most prevalent forms in 2025:
- Emails: Fake invoices mimicking Norton, McAfee, Microsoft, PayPal, or Adobe, often with urgent subject lines like “Payment Failed: Action Required.”
- Browser Popups: Full-screen alerts that freeze your browser, displaying messages like “Your McAfee Protection Has Expired! Call Now.” These may use JavaScript to lock the screen.
- Phone Calls: Scammers pose as tech support, claiming you’ve been “overcharged” for a subscription and offering a refund to gain trust.
- Text Messages (Smishing): SMS claiming your Netflix or Dropbox subscription auto-renewed for $499.99, urging you to call or click a link for a refund.
- AI-Generated Voicemails: Emerging in 2025, scammers use AI tools like ElevenLabs to create realistic voicemails mimicking brand representatives, urging callbacks.
Example: A 2025 X post reported a surge in smishing scams targeting PayPal users, with texts claiming, “Your PayPal subscription renewed for $299. Call 1-888-555-XXXX for a refund.”
Why It Works
These scams are effective due to psychological and technical tactics:
- Brand Trust Exploitation: Scammers use logos and names of trusted companies (Norton, PayPal, etc.) to lower suspicion.
- Urgency and Fear: Phrases like “Your device is at risk!” or “FINAL NOTICE” trigger panic, exploiting the scarcity principle.
- Technical Jargon: Official-sounding terms like “auto-renewal failure” or “system vulnerability” confuse non-technical users.
- Fake Refunds as Bait: Offering a refund appeals to victims’ desire to recover money, a tactic rooted in the reciprocity bias.
- Targeting Vulnerabilities: Scammers target demographics like seniors, who may fear tech issues, or small businesses worried about downtime.
Psychological Insight: According to a 2023 University of Cambridge study, scams exploit the “authority bias,” where victims trust messages appearing to come from legitimate companies, especially under time pressure.
How to Spot It
Use this checklist to identify subscription renewal scams:
| Red Flag | Example |
|---|---|
| No Active Subscription | You receive a Norton renewal notice but don’t use Norton. |
| Suspicious Sender | Email from support@security-update247.com instead of norton.com. |
| High Charges | Invoice claims $349.99 for a basic antivirus subscription. |
| Urgent Language | Words like “URGENT,” “FINAL NOTICE,” or “IMMEDIATE ACTION REQUIRED.” |
| Call for Refunds | Refunds require calling a number, unlike legitimate vendors. |
| Suspicious Attachments | Invoices as Word/PDF files with generic logos or misspellings. |
| Poor Grammar/Design | Typos or mismatched fonts in emails or invoices. |
Technical Tip: Check email headers for spoofing. Right-click the email, select “View Source,” and look for a mismatch in the “From” and “Return-Path” fields. Tools like CyberChef can decode URLs in suspicious links.
How to Stay Safe
Protect yourself with these steps:
- Verify Directly: Log into the official website (e.g.,
norton.com,paypal.com) to check your subscription status. Never use links or numbers from unsolicited messages. - Avoid Unsolicited Calls: Never call numbers in unexpected emails, texts, or popups. Search for the company’s official support number independently.
- Block Remote Access: Don’t install remote access tools (e.g., TeamViewer, AnyDesk) unless you initiated contact with a verified vendor.
- Report and Block: Mark scam emails as spam or phishing in your email client. Report texts to your carrier by forwarding to 7726 (SPAM).
- Secure Accounts: Enable multi-factor authentication (MFA) on bank accounts and use a password manager like Bitwarden for unique, strong passwords.
- Scan for Malware: Use free tools like Malwarebytes or Windows Defender to scan for keyloggers or ransomware after suspicious interactions.
- Recover from Fraud: If you’ve shared financial info, contact your bank immediately, freeze accounts, and report to
identitytheft.gov(US),cyber.gov.au/report-and-recover/report(AUS) or equivalent in your country.
Tool Recommendation: Install uBlock Origin (browser extension) to block malicious popups and ads that deliver fake alerts.
Tools and Resources
Enhance your defenses with these free or open-source tools:
- Malwarebytes: Free antivirus for scanning and removing malware.
- CyberChef: Analyze suspicious URLs or email headers (
https://gchq.github.io/CyberChef/). - Have I Been Pwned: Check if your email was exposed in a breach (
haveibeenpwned.com). - uBlock Origin: Block malicious ads and popups (available for Chrome, Firefox).
- TryHackMe: Learn to spot phishing with free cybersecurity labs (
tryhackme.com).
FAQ: Common Myths About Subscription Scams
“I’m safe because I have antivirus software.”
Antivirus software protects against malware but not social engineering scams. Scammers rely on you giving them access or info voluntarily. Always verify claims directly.“Only non-techy people get scammed.”
Anyone can fall for scams, especially with AI-generated emails or calls that seem legitimate. In 2024, 20% of tech professionals reported being targeted by phishing scams (Source: SANS Institute).“I can trust refund offers.”
Legitimate companies process refunds via their official website or app, not through unsolicited calls or remote access. Always initiate contact yourself.Key Takeaway: Subscription Scam Red Flags
- Fake renewal invoices for antivirus, streaming, or cloud services
- Urges you to call a number or click a link for payment/refunds
- Requests remote access or banking details
- Emails/texts with odd addresses, typos, or generic logos
- Real vendors don’t demand payment via unsolicited calls
- Quick Action: Always verify subscriptions directly on the official website.
Further Reading and Community
- X Posts: Follow @CyberWatchDog or @ScamBusterX for real-time scam alerts.
- Learning Platforms: TryHackMe (
tryhackme.com) or Cybrary (cybrary.it) for free cybersecurity training. - Communities: Join the UMBC CyberDawgs Discord for beginner-friendly cybersecurity discussions.
- Resources: Check OWASP’s Top 10 (
owasp.org) for broader web security tips orPayloadsAllTheThingson GitHub for scam examples.

Crypto Giveaway Scams — Elon’s Not Sending ETH
These scams promise free cryptocurrency in exchange for a small upfront payment or ask users to “verify” a wallet.
They often impersonate tech CEOs, crypto platforms, or influencers to appear credible.
How the Scam Works
You see a message like:
Elon Musk is giving away 10,000 ETH!
Send 0.5 ETH to the address below and receive 5 ETH back instantly!
Or:
Binance Anniversary Giveaway
Connect your wallet to claim your airdrop.
Once you send funds or connect your wallet:
- You lose the funds permanently
- If you sign a smart contract, scammers can drain your wallet
- Your wallet may be cloned or phished for future use
Common Delivery Methods
- YouTube livestreams faking Tesla or SpaceX events
- Fake Twitter/X replies from verified-looking accounts
- Email blasts using spoofed addresses (e.g.,
noreply@binance-airdrop.com) - Discord, Telegram, or Reddit messages offering free NFTs or giveaways
- Fake wallet popups on compromised crypto sites
Why It Works
- Uses celebrity trust (Elon Musk, Vitalik Buterin, MrBeast, etc.)
- Plays on greed — “get rich fast” or “limited-time airdrop”
- Looks legitimate due to branding, logos, and real video footage
- Fake websites often closely match the real domains
- Targets users who already own crypto and are used to online promotions
Real-World Example
A YouTube ad claims Tesla is launching a new crypto.
The stream shows real Elon Musk interviews, with a “QR code” for viewers to scan and send crypto.
Thousands send funds — and none receive anything back.
The wallet is controlled by the scammer, and transactions are irreversible.
How to Spot It
- Anyone asking you to send crypto to get more back is a scam
- Giveaways requiring wallet connection or seed phrase input
- URLs that are slightly off (e.g.,
binánce.cominstead ofbinance.com) - Streams with chat disabled or flooded with fake praise
- Overuse of emojis, countdowns, or “only X left” gimmicks
- Messages from unfamiliar Telegram or Discord groups
How to Stay Safe
- Never send crypto in response to a giveaway
- Use wallet browser extensions that detect malicious contracts
- Bookmark real crypto platforms — don’t rely on ads or messages
- Double-check official social accounts before trusting any campaign
- Don’t connect your wallet to unfamiliar dApps or sites
- Enable withdrawal delays and 2FA on crypto exchange accounts
Key Takeaway: Crypto Giveaway Scam Signs
- Promises of free ETH, BTC, or NFTs in return for sending crypto
- Uses celebrity names and real interviews to look legit
- Fake livestreams or hacked social accounts promote the scam
- Wallet connection or QR code leads to theft
- Real platforms never ask you to “verify” wallet with funds
- Once you send crypto, it’s gone — no recovery

Call Center Tech Support Scams — What They Say and Why
These scams involve fake support calls, popups, or voicemails claiming your device is infected or compromised.
The goal is to scare you into calling a “technician” — who then steals access, data, or money.
How the Scam Works
It starts with:
- A browser popup that locks your screen and says “Do not close — your computer is infected!”
- A voicemail claiming to be from Microsoft or Norton support
- An unsolicited call saying “your system is reporting critical errors”
Once you call back or stay on the line, they:
- Ask you to download remote control tools (e.g., AnyDesk, TeamViewer)
- Show fake “system errors” using built-in tools like Event Viewer or Task Manager
- Claim your license expired or your network is compromised
- Request payment for a “one-time fix” or multi-year support plan
- Sometimes offer a refund, then create a fake “banking over-refund” scenario to steal more
Where These Scams Show Up
- Fake antivirus popups on shady websites or ads
- “System scan” overlays that freeze your screen
- Voicemails saying your subscription is expiring
- Search engine ads for fake Microsoft or Norton support
- Robocalls spoofing real company names and numbers
Why It Works
- Preys on fear of viruses or financial loss
- Uses technical language to confuse non-technical users
- Sounds urgent and scripted (“Your system has been flagged for data exfiltration”)
- Impersonates trusted names like Microsoft, McAfee, or Apple
- Pushes for quick action to avoid “complete data loss”
Real-World Example
A popup takes over your browser with the Windows Defender logo and this message:
CRITICAL ALERT FROM MICROSOFT
Your computer has been blocked.
Call support at 1-888-123-4567 to remove the threat.
When you call, the scammer walks you through downloading remote access software and charges $299 for the “fix.”
In the background, they may quietly exfiltrate files or install malware.
How to Spot It
- Real tech companies never initiate unsolicited support calls
- Popups that prevent you from closing the browser are fake
- Support numbers found in error messages are always fake
- Fake “Event Viewer” warnings like “Error ID 7001” mean nothing
- Repeated urging to “act now” is a red flag
- Any mention of gift cards or wire transfers for payment = scam
How to Stay Safe
- Never call numbers listed in popups or error screens
- Don’t let strangers remote into your computer — no matter how convincing
- Close the browser or reboot if you see a suspicious message
- Run a real antivirus scan after any weird popup or redirect
- Block known scam numbers and report them to authorities
- Educate family or older users who are common targets
Key Takeaway: Tech Support Scam Warning Signs
- Fake popups or voicemails claim your device is infected
- Prompts you to call a support number — always fake
- Uses fear to push remote access or payment
- Real companies don’t cold call or lock your browser
- Asks for payment via gift cards or wire
- Event Viewer errors or CMD output are misused to scare
- Always verify through official websites only
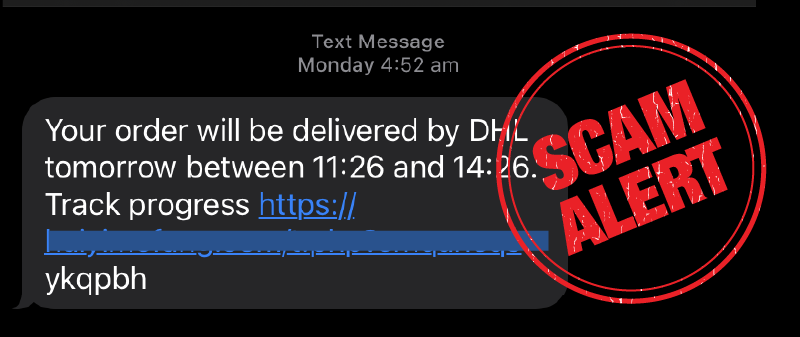
“Your Parcel Is Held” Text Messages Explained
These SMS scams claim a package couldn’t be delivered and urge you to click a link.
Once clicked, the site may steal credentials, credit card info, or prompt malware downloads.
How the Scam Works
You receive a text message like:
Royal Mail: Your parcel is awaiting delivery.
Please confirm your address and pay the £1.99 handling fee: [fake-link.com]
Or:
AUPost: Delivery attempt failed.
Reschedule at [short.url/xyz123]
The link leads to a fake parcel tracking site that:
- Looks like the real postal service website
- Asks you to input name, address, DOB, and card details
- May install malicious APKs on Android devices
- Sends data to the attacker in real time
Why It Works
- Everyone orders online — it feels timely and relevant
- Fake sites look real (logos, tracking bars, forms)
- Small “fee” sounds harmless, making you more likely to pay
- Urgency (24-hour delivery window) increases clicks
- Targets both consumers and business employees
Real-World Example
A victim receives:
DHL: We attempted to deliver your package, but no one was home.
Reschedule now:dhl-tracking-secure.com
The user clicks, fills out a fake form, and enters card details.
Days later, their card is charged with multiple unauthorized purchases.
On Android, the link also installs spyware that silently monitors messages.
How to Spot It
- Domain is unfamiliar or slightly altered (e.g.,
auspost-track.delivery) - Fee requested for standard delivery or customs is suspicious
- Shortened links hide the real destination (bit.ly, tinyurl, etc.)
- SMS arrives even if you didn’t order anything recently
- Grammar or formatting errors in the message
- App download prompt outside of Play Store
How to Stay Safe
- Never enter payment or personal info via SMS links
- Always verify delivery status through official tracking portals
- Report fake parcel texts to your country’s scam watchdog or telco
- On Android, disable unknown app installs from browsers
- Use SMS spam filtering tools or block known scam numbers
Key Takeaway: Parcel Scam Red Flags
- SMS claims your parcel is held or needs redelivery
- Asks for a small fee or verification via a fake link
- Site steals personal or payment details
- Android phones may be prompted to install spyware
- Real delivery companies don’t charge random fees via SMS
- Always verify parcels through official channels
Romance & Investment Scam Red Flags
These scams build emotional trust — then exploit it to steal money, crypto, or personal information.
They can last days, weeks, or even months before the final financial hook appears.
How the Scam Works
- Scammer meets the victim via dating apps, social media, or messaging platforms
- Builds emotional connection quickly — flattery, daily messages, fabricated life stories
- Introduces investment opportunity (usually crypto) or claims they need urgent financial help
- Victim is persuaded to send money, crypto, or gift cards
- The scammer disappears — or keeps asking for more, promising love or profit
Common Variants
- Crypto love scams: They convince victims to “invest” using a fake trading app
- Emergency scams: Scammer claims they’re stuck overseas and need help
- Inheritance scams: Fake legal claims that require upfront fees
- Pig butchering: Long-term relationship grooming ending in major financial loss
Why It Works
- Exploits loneliness or vulnerability
- Creates trust through shared interests and fake backstories
- Uses time pressure — “limited-time crypto trade” or “emergency medical bill”
- Often impersonates real people (stolen photos, fake credentials)
- Victims are emotionally invested, which overrides logical red flags
Real-World Example
A woman meets a man via Instagram. He’s kind, wealthy, and “cares deeply.”
He shares screenshots of his crypto gains and convinces her to join.
She downloads an app he recommends and deposits $1,000.
The app shows returns — but when she tries to withdraw, she’s told to deposit more.
Eventually, she loses over $20,000 and never hears from him again.
How to Spot It
- They avoid video calls or face-to-face meetings
- They quickly profess strong feelings or ask deeply personal questions
- They talk about crypto or business opportunities early on
- Their social media presence feels shallow or inconsistent
- They ask for secrecy or discourage telling friends/family
- Requests for crypto, gift cards, or money transfers always follow
How to Stay Safe
- Be skeptical of quick romantic escalations from strangers
- Don’t send money or invest in anything from online-only relationships
- Reverse-image search their photos to check for fakes
- Use reputable dating platforms with verification
- Talk to someone you trust before sending money
- Report suspicious profiles to platforms and scam watch groups
Key Takeaway: Romance/Investment Scam Red Flags
- Relationship moves quickly, with flattery and emotional intensity
- Talk of crypto investing or business opportunities arises
- They avoid meeting in person or video calling
- Fake apps or trading platforms are introduced
- You’re asked to send money, then pressured to send more
- Emotional manipulation is used to suppress doubt
Final Thoughts
Scammers adapt quickly, leveraging urgency, trust, and emotion to manipulate victims. By recognizing patterns across different scam types — fake renewals, crypto giveaways, tech support calls, delivery SMS, and romance investments — you can strengthen your defenses.
Golden Rule: If it sounds urgent, too good to be true, or asks for money/crypto/gift cards — pause, verify directly with the real company, and never act on impulse.
Share this guide with colleagues, friends, or family — awareness is the strongest first line of defense.


