Sextortion Scams Are Back
What They Are, How They Work, and Why They’re So Effective
Sextortion scams are resurfacing — exploiting fear, shame, and privacy for profit. Learn how they work, why they’re effective, and how to protect yourself.

Sextortion scams exploit the most powerful human emotions — fear, shame, and embarrassment — to extort money from victims. This guide explores how threat actors operate, why these scams still work, and how you can protect yourself from falling into their trap.

Introduction
In the modern cyber threat landscape, few scams are as personal and manipulative as sextortion. These scams don’t rely on zero-days or malware, but on psychological warfare — leveraging fear and shame to force victims into paying ransom in cryptocurrency.
Sextortion scams have resurfaced globally in 2025, using more polished templates, localized translations, and even unique Bitcoin wallets for tracking. Reports from European spam telemetry feeds show a sharp spike in sextortion email campaigns, with victims still sending payments despite widespread awareness.
What Is Sextortion?
Sextortion is a form of blackmail where cybercriminals claim to possess compromising videos or images of their victim and threaten to release them unless paid.
The majority of these cases are fake — no real compromise has occurred. Attackers mass-distribute spam emails pretending to have hacked webcams or screens, manipulating victims through psychological pressure rather than technical compromise.
The name itself merges sex and extortion, accurately reflecting its coercive nature. Although there are isolated real-world cases involving genuine compromise, most sextortion emails are purely fear-based scams.
How the Scam Works
While the specifics may vary, sextortion campaigns generally follow the same structure:
-
The Threat Email Arrives
Victims receive an email claiming their system has been hacked and their webcam accessed.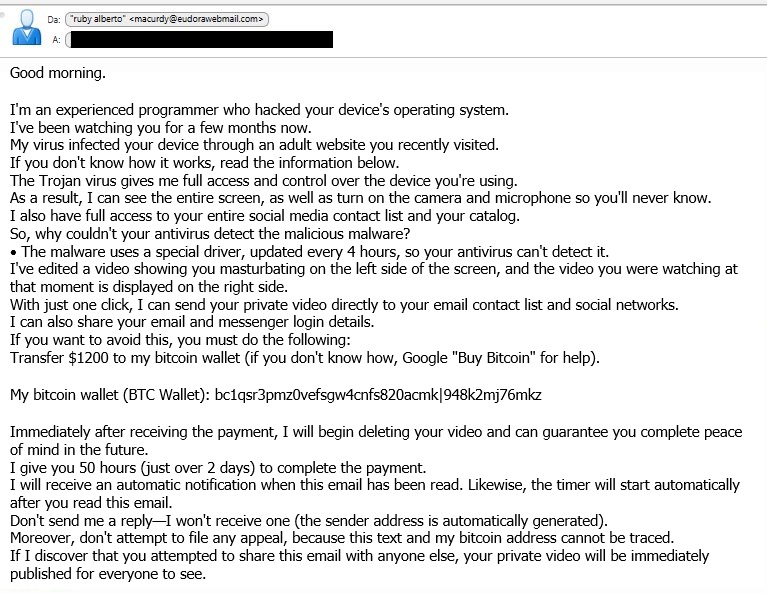
-
False Technical Claims
The message references supposed Trojans, backdoors, or remote desktop access to sound credible. Some even claim that the malware updates “every 4 hours.” -
Ransom Demand
Victims are told to pay a ransom — typically $500 to $2,000 in Bitcoin — to prevent public release of the alleged footage.
Example wallet:bc1qsr3pmz0vefsgw4cnfs820acmkl948k2mj76mkz -
Urgency and Fear
The email sets a short deadline (often 24–48 hours) to pressure the victim into paying without verifying the claim. -
False Proof of Compromise
In some versions, the attacker includes the victim’s real password (from old data breaches) or claims to have access to their social media contacts.
Despite the lack of evidence, these tactics are effective because they exploit human emotion, not logic.
Case Study
A sample email shows the attacker using macurdy@eudorawebmail.com and referencing local ISP details to increase credibility.
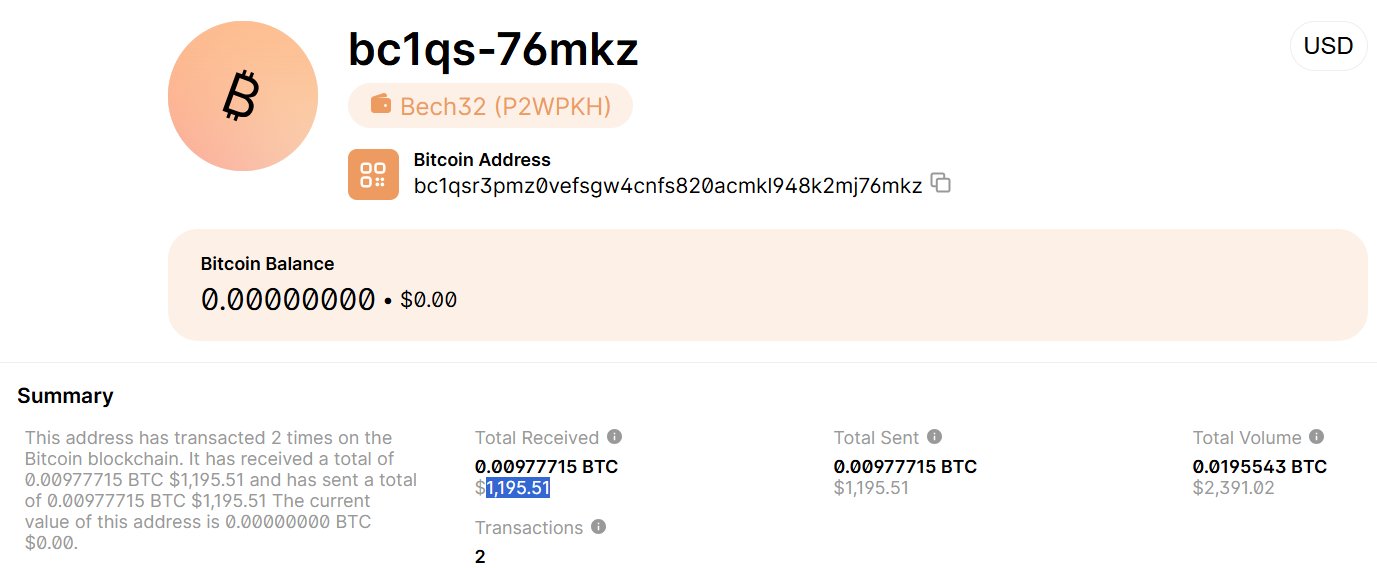
The Bitcoin address linked to this campaign received two confirmed payments, totaling $1,195 USD, before the funds were quickly withdrawn — a common sign of automated laundering or cryptocurrency mixers.
Key traits observed:
- Generic but localized subject lines
- Free webmail sender domains
- Claims of full webcam and microphone access
- Bitcoin-only payment method
- Recycled text templates translated into multiple languages
The success of such low-effort campaigns underscores how effective fear-based manipulation remains.
Why Victims Still Fall for It
Even tech-savvy individuals can panic when confronted with such personal threats. Common psychological levers include:
- Embarrassment — Fear of social judgment or exposure.
- Credibility Illusion — Use of real passwords from old leaks.
- Urgency — Pressure to pay before “the video is released.”
- Isolation — Victims are warned not to tell anyone.
This combination can trigger a “fight or flight” response, impairing rational decision-making.
The Technical Infrastructure Behind Sextortion Campaigns
Despite the personal tone, sextortion operations are industrialized. Threat actors run these scams as automated spam enterprises, using:
- Mass Mailing Systems – Botnets and compromised servers push millions of messages daily.
- Localization Engines – Automatic translation makes emails appear locally written.
- Disposable Cryptocurrency Wallets – New Bitcoin addresses are generated per victim batch.
- Money Laundering Chains – Received funds are quickly moved through mixers or privacy coins like Monero.
There is no real malware infection or system compromise. The entire operation runs on automation, deception, and fear.
The Scale and Profitability of Sextortion
Although conversion rates are small (around 0.05%–0.3%), volume ensures profit. For every million messages sent, dozens of victims may pay — enough to sustain operations with minimal cost.
Sextortion spam peaks roughly every 6–8 months and correlates strongly with cryptocurrency market surges, when ransom values are higher.
The campaign mentioned earlier is a textbook example: two payments totaling over $1,000 show that awareness alone doesn’t stop fear-driven decisions.
How to Protect Yourself
-
Stay Calm and Do Not Pay
No hacker has compromised your camera. Paying validates your address and funds criminal activity. -
Do Not Respond
Any reply confirms that your inbox is active, inviting further targeting. -
Change Compromised Passwords
If a real password appears in the email, it likely came from a historical data breach. Reset it immediately and enable multi-factor authentication. -
Report and Delete
Mark the message as spam and report it to national cybercrime agencies. -
Educate and Normalize Discussion
These scams thrive on silence. Talking openly about them removes their power.
Recognizing Sextortion Red Flags
| Indicator | Explanation |
|---|---|
| Old password shown | Taken from a past data breach. |
| Cryptocurrency payment demand | Bitcoin or Monero only. |
| Short deadline | Pressure tactic to force a decision. |
| Overly technical language | Meant to sound credible. |
| Claims of webcam footage | Never actually exists. |
The Role of Cryptocurrency
Bitcoin enables anonymity that traditional banking cannot. Attackers typically:
- Generate a new wallet per campaign batch.
- Withdraw funds within hours.
- Route through mixers or exchanges that avoid KYC rules.
The observed wallet (bc1qsr3pmz0vefsgw4cnfs820acmkl948k2mj76mkz) demonstrates a clear pattern of instant withdrawal — a strong indicator of automated laundering systems.

The Bigger Picture
Sextortion scams are part of a broader trend: the weaponization of emotion in cybercrime.
Unlike phishing or malware, these attacks exploit human vulnerability, not system flaws.
They remind us that cybersecurity awareness must address not only technology, but psychology.
Key Takeaways
- Sextortion emails are mass scams, not personal hacks.
- They exploit fear, shame, and urgency — not vulnerabilities.
- Bitcoin remains the preferred payment method for anonymity.
- Education and awareness are the most effective defenses.
- The best response is simple: don’t panic, don’t pay, don’t reply.
Cybercriminals don’t need malware to cause harm — only fear. Awareness and open discussion are the strongest tools we have to shut down sextortion for good.


