Weekly Threat Trends — Week Commencing 12th January 2026
The second full week of 2026 is already busy: actively exploited vulnerabilities in core infrastructure and developer tooling, targeted ransomware against healthcare and claims processors, major breaches in education and space, and a clear shift in executive risk focus towards AI-driven threats and cyber-enabled fraud.

The week of 12–18 January 2026 feels like the moment the holiday afterglow wears off.
Patch Tuesday shipped with an actively exploited Windows zero-day. Ransomware crews hit healthcare and claims-management firms. Education and space agencies disclosed significant breaches. CISA added new developer tooling to its Known Exploited Vulnerabilities list. And the first wave of 2026 threat and risk reports are unanimous about one thing:
The centre of gravity is shifting towards identity, AI-accelerated tradecraft, and data-centric extortion — while all the “old” problems (unpatched vulns, phishing, ransomware) remain very much alive.
Top Trends at a Glance
- Actively Exploited Core Vulns – a Windows info-disclosure zero-day under active attack, plus a Gogs Git service RCE added to CISA’s KEV with no patch yet.
- Targeted Ransomware in Healthcare and Services – CrazyHunter hitting hospitals, TridentLocker hitting a global claims processor, against a backdrop of >8,000 ransomware attacks in 2025.
- High-Impact Breaches in Education and Space – Victorian government schools and the European Space Agency both disclosing compromises of sensitive systems and student/staff data.
- “Hackers Getting Hacked” and Privacy Scrutiny – BreachForums’ own user database leaked, and Lloyds facing an ICO probe over internal data use in pay talks.
- AI, Automation and Executive Risk Re-Prioritisation – 2026 risk surveys elevating cyber-enabled fraud and AI-related vulnerabilities above “classic” ransomware.
- SEO Poisoning and Loader Evasion on the Web Front – Black Cat data-stealer infections via poisoned search results, plus GootLoader abusing malformed ZIP archives to dodge detection.
Exploited Vulnerabilities: Windows Zero-Day and Gogs RCE
The first Patch Tuesday of 2026 landed hard. Microsoft and US agencies warned that a Windows information-disclosure bug, CVE-2026-20805, is already being exploited in the wild. :contentReference[oaicite:0]{index=0}
Key points:
- The flaw affects supported Windows versions and was patched as part of January’s updates.
- Attackers are leveraging it in chained exploits, using info-disclosure to improve reliability of subsequent RCE or privilege-escalation steps.
- CISA echoed the urgency by pushing agencies to apply January patches quickly. :contentReference[oaicite:1]{index=1}
At the same time, CISA added a Gogs remote-code-execution vulnerability to its Known Exploited Vulnerabilities (KEV) catalogue, warning that:
- The bug allows unauthenticated or low-privileged attackers to execute arbitrary code on affected Gogs instances.
- Exploitation is active, and no official patch is available yet; mitigations revolve around upgrading to safe forks or applying community workarounds. :contentReference[oaicite:2]{index=2}
Why this matters:
- Gogs and similar self-hosted Git services underpin internal source code, IaC, and CI/CD in a lot of orgs.
- A compromised Gogs instance is effectively root access to your software supply chain:
- Attackers can backdoor repos.
- Inject malicious dependencies.
- Steal secrets stored in code or build configs.
For this week, patching and mitigation priorities are clear:
- Treat CVE-2026-20805 as a fast-track patch for Windows.
- For any self-hosted Git (Gogs, Gitea, legacy GitLab, etc.):
- Check versions against KEV and vendor advisories.
- Lock down external exposure and enforce strong auth.
- Assume compromise if you find an unpatched, internet-exposed instance — and respond accordingly.
Ransomware: Healthcare, Claims Management and 8,000+ Victims
Ransomware did not wait long to make its presence felt in 2026.
CrazyHunter and Healthcare
Industrial Cyber reporting this week highlights the CrazyHunter ransomware group:
- At least six healthcare organisations in Taiwan confirmed as victims.
- Operators using advanced intrusion tactics rather than smash-and-grab brute forcing. :contentReference[oaicite:3]{index=3}
- The campaign reinforces how healthcare remains a magnet:
- High data sensitivity.
- Limited patching windows.
- Strong pressure to restore services quickly.
TridentLocker vs Sedgwick
On the services front, a breach disclosure around global claims-management firm Sedgwick shows:
- The TridentLocker ransomware group claims to have exfiltrated sensitive data from systems supporting government services operations.
- Ransomware was reportedly deployed after data theft — classic modern double extortion. :contentReference[oaicite:4]{index=4}
This is entirely in line with Emsisoft’s State of Ransomware in the US 2025 report:
- Over 8,000 organisations claimed as ransomware victims in 2025, up from ~6,000 in 2024.
- Active groups increased by ~30%, with crews like Qiling, Akira, Cl0p, Play and Safepay among the most active. :contentReference[oaicite:5]{index=5}
Law Enforcement and Insider Abuse
There is some good news: two US cybersecurity professionals recently pleaded guilty for their role in BlackCat/ALPHV ransomware operations, in a case that leveraged their insider knowledge of security tooling to facilitate attacks. :contentReference[oaicite:6]{index=6}
This underscores:
- Law-enforcement pressure on big brands works — but the ecosystem is broad and resilient.
- Insider risk applies even to people working inside the security industry.
For defenders this week:
- Healthcare and critical services should validate:
- Exposure of remote-access paths.
- EDR coverage and logging on edge systems and domain controllers.
- Any incident playbook for ransomware needs to treat:
- Data exfiltration as a first-class concern.
- Insider threat and abuse of security tools as a real possibility.
Education, Space and a Wide Breach Surface
On the breach side, three very different victims tell the same story: no sector is off-limits.
Victorian Government Schools
In Australia, the Victorian Department of Education disclosed that hackers accessed:
- Names.
- School-issued email addresses.
- Encrypted passwords.
- School names and year levels.
…for current and former students at all Victorian government schools. :contentReference[oaicite:7]{index=7}
Key details:
- The breach occurred via a compromised school network, hitting a departmental database.
- Officials say they have identified the breach source and implemented safeguards, and that there is no evidence (yet) of public data release.
- Password resets are underway across affected institutions.
The scale is significant — reports suggest hundreds of thousands of students may be impacted — and the data involves minors, which carries elevated privacy and regulatory sensitivity.
European Space Agency (ESA)
A separate roundup of January breaches notes that the European Space Agency (ESA) also suffered a cyber attack:
- The incident compromised servers used for collaborative engineering solutions within the scientific community.
- ESA has confirmed the breach and is investigating the extent and impact. :contentReference[oaicite:8]{index=8}
While details are still emerging, it underscores how R&D and scientific collaboration platforms are valuable targets — often with weaker perimeter controls than mission-critical operational systems.
BreachForums Breached
Finally, even the attackers’ hangouts are not immune. Underground marketplace and hacking hub BreachForums disclosed a breach:
- A data dump of around 324,000 user accounts — including usernames, registration dates and IP addresses
— was leaked in an archive named
breachedforum.7z. - The data appears to come from an August 2025 incident when the forum was being rebuilt after a raid, and a database folder was exposed in an unsecured location.
- Over 70,000 non-loopback IPs may be usable for deanonymisation and law-enforcement work. :contentReference[oaicite:9]{index=9}
The irony is obvious, but the lesson is serious:
- Attack infrastructure and criminal communities carry their own exposure.
- Law-enforcement and intel teams will likely mine this data for years to come.
For blue teams, the takeaway from all three:
- Student records, scientific collaboration data, and even “metasystems” like forums can be stepping stones into broader ecosystems.
- Breach response must include:
- Identity and password hygiene.
- Clear messaging for affected users (especially parents and minors).
- Realistic assessment of data-reuse risk (credential stuffing, targeting, fraud).
Privacy, Data Use and Regulatory Pressure
Not every incident this week involved an external attacker. In the UK, Lloyds Banking Group is under scrutiny from the ICO for allegedly using aggregated data from 30,000 staff bank accounts in pay negotiations:
- The bank reportedly analysed employee financial data to argue that lower-paid staff were better off than the general public.
- As most staff hold accounts with the bank, the ICO is investigating whether this data use breached privacy law. :contentReference[oaicite:10]{index=10}
The case highlights:
- Even internal analytics on first-party data can cross regulatory lines if consent and purpose are not clear.
- Privacy regulators are increasingly willing to explore non-breach data misuse scenarios.
Add this to the growing list of regulatory moves:
- Mandatory ransomware/extortion reporting in several jurisdictions.
- Tougher breach-notification timelines.
- Executive accountability discussions in national cyber strategies. :contentReference[oaicite:11]{index=11}
For 2026, privacy risk is no longer just about “did someone steal it?” — it is equally about “did we use it in ways we can justify?”
AI, Automation and 2026 Risk Priorities
On the forward-looking side, several 2026 threat prediction reports landed this week.
A World Economic Forum-aligned analysis of executive views shows:
- In 2025, CEOs ranked ransomware, cyber-enabled fraud, and supply-chain disruptions as their top cyber risks.
- For 2026, the top three shift to:
- Cyber-enabled fraud.
- AI-related vulnerabilities.
- Traditional software vulnerabilities.
- Among CISOs, ransomware still tops the list, followed by supply-chain and software vulnerabilities. :contentReference[oaicite:12]{index=12}
Separately, security vendors and researchers highlight:
- Ransomware evolving towards targeted disruption and data destruction, not just encryption. :contentReference[oaicite:13]{index=13}
- Rapid, often uncontrolled adoption of AI and automation:
- Expanding the internal attack surface.
- Blurring the boundary between “inside” and “outside”.
- Making social engineering more convincing and scalable. :contentReference[oaicite:14]{index=14}
Taken together:
- Executives are worried less about any single family of malware, and more about:
- Being defrauded at scale.
- Making big mistakes with AI adoption.
- Getting caught out by yet another high-impact vulnerability.
- Security programs that stay focused only on “catch the ransomware” will miss the fraud, AI and supply-chain angles that leadership now cares about.
This week is a good moment to align:
- Threat intel and DFIR teams (what we are actually seeing).
- Risk and governance teams (what boards and regulators are worried about).
- AI/innovation teams (what tools and agents are being deployed in 2026).
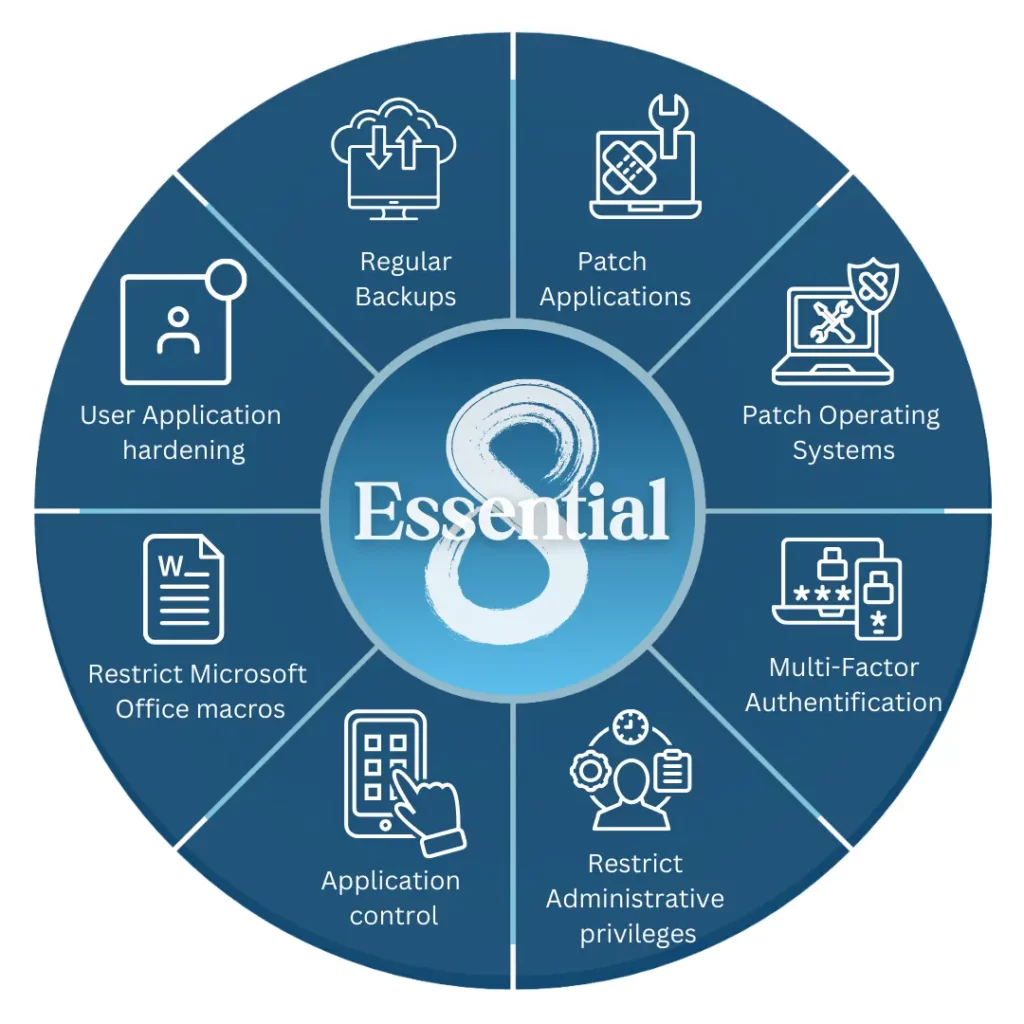
OT and Critical Infrastructure: Guidance and Hacktivists
CISA and international partners published new guidance for industrial and OT practitioners, outlining eight key principles for defending connected OT systems and making “confident, security-led decisions” about risk.
The advisory follows earlier warnings about pro-Russian hacktivist intrusions targeting critical infrastructure worldwide. :contentReference[oaicite:15]{index=15}
In parallel, we see:
- Ransomware like CrazyHunter targeting healthcare with increasingly mature intrusion tactics. :contentReference[oaicite:16]{index=16}
- Vendors emphasising security convergence across IT, cloud and OT segments.
For OT defenders, the early 2026 message is:
- Hacktivism, ransomware crews, and nation-state actors are all probing the same ground.
- Practical steps (network segmentation, strict remote-access controls, asset visibility) remain the foundation.
- Guidance from national cyber centres is not theory — it is battle-tested minimums.
SEO Poisoning, Malformed ZIPs and the Browser Front
On the web front, the week continues two important trends:
SEO Poisoning and Data-Stealers
Chinese CERT and ThreatBook reporting (summarised by The Hacker News) shows a group dubbed “Black Cat” (not the ALPHV ransomware crew) using SEO poisoning and fake software downloads to infect roughly 277,800 systems in China with data-stealing malware:
- Victims are lured by search results for popular software.
- The payload steals browser data, keystrokes, and clipboard contents, then connects back to a hard-coded
C2 (
sbido[.]com:2869). :contentReference[oaicite:17]{index=17}
GootLoader’s Malformed ZIP Archives
The long-running GootLoader malware family has been observed using a new anti-analysis trick:
- Malformed ZIP archives created by concatenating 500–1,000 ZIP files.
- The structure is designed to confuse scanners and analysts, hiding the malicious JavaScript loader deeper inside. :contentReference[oaicite:18]{index=18}
Both campaigns underline:
- The browser is a primary battleground:
- Search results lead to infection.
- ZIP archives remain the workhorse of initial access.
- “Just block EXEs” is nowhere near enough when:
- Payloads arrive as scripts and archives.
- Users are conditioned to trust downloads they “found themselves” via Google or Bing.
This week’s practical takeaway:
- Tighten browser extension and download policies.
- Use DNS/web filtering that can react to:
- Sudden spikes of traffic to newly registered domains.
- Known malvertising and SEO-poisoning infrastructure.
- Educate users that:
- “First search result” ≠ safe.
- Vendor sites and official stores are the only acceptable sources for software.
Actions for the Week of 12–18 January
To turn this week’s noise into action, here are concrete moves that fit into normal operations:
Patch and Mitigate
- Prioritise January Patch Tuesday, especially:
- Windows CVE-2026-20805.
- Audit self-hosted Git (Gogs, Gitea, etc.) exposure:
- Compare versions against KEV.
- Restrict internet access.
- Begin planning for upgrades or migration if you’re on affected builds.
Harden Against Ransomware and Extortion
- Validate:
- EDR coverage on domain controllers, hypervisors, and backup servers.
- Offline/immutable backups for key systems.
- For healthcare and public services:
- Rehearse incident comms and continuity plans specifically for data exfil + encryption scenarios.
Respond to the Breach Climate
- If you operate in education or handle minors’ data:
- Review identity and password management for student accounts.
- Ensure clear parent/guardian comms templates exist.
- For all orgs:
- Re-check breach playbooks for:
- Data-classification awareness.
- Regulator-notification steps and timelines.
- Re-check breach playbooks for:
Align on AI and Fraud Risk
- Meet with risk/governance or leadership to:
- Share the 2026 risk priority shift (fraud and AI vulnerabilities).
- Map where your current controls align — and where they don’t.
- Start or refine a Shadow AI inventory:
- Which GenAI tools your staff are using.
- Where data may be flowing today without policy.
Strengthen OT and Web Fronts
- For OT/ICS:
- Compare your practices against the new CISA/partner guidance and identify 1–2 gaps to close this quarter.
- For web/browser:
- Tighten extension allow-lists.
- Add SEO-poisoning and malvertising indicators to hunts and proxy analytics.
Closing Thoughts
The week commencing 12th January 2026 doesn’t have a single “big bang” incident — instead, it gives a clear cross-section of where the fight is heading:
- Exploited vulns in core platforms and development tooling.
- Ransomware that prefers careful intrusion and data theft over smash-and-grab.
- Breaches that reach from school networks to space agencies to underground forums.
- AI and fraud climbing to the top of executive worry lists.
- Browsers and search results quietly becoming primary infection vectors.
The good news is that the countermeasures are not mysterious:
Patch what’s being exploited.
Lock down the systems that create and move your code.
Treat identity and data as first-class security domains.
And pay down observation debt so you can actually see, with evidence, what happened when things go wrong.
If you can move even a little on those fronts this week, you’re starting 2026 in the right direction.