Weekly Threat Trends
Week Commencing 20 Oct 2025
Analysis of the week’s dominant cyber threats — from fake browser updates and supply-chain breaches to scam evolutions exploiting trust in government and payment systems.

A concise, evidence-based overview of the key threats, tactics, and trends observed between 20–26 October 2025 — focused on translating technical noise into clear awareness.
Top Trends at a Glance
- Fake browser and software update campaigns push RedLine and new stealer variants.
- Compromised ad-networks deliver malicious installers through legitimate websites.
- Government-themed smishing resurges, targeting tax refunds and ID verification.
- Telegram and Discord continue to host stealer payloads and phishing kits.
- QR-phishing and voice-clone vishing maintain steady presence, showing long-term adoption.
1. Fake Browser Update & Malvertising Campaigns
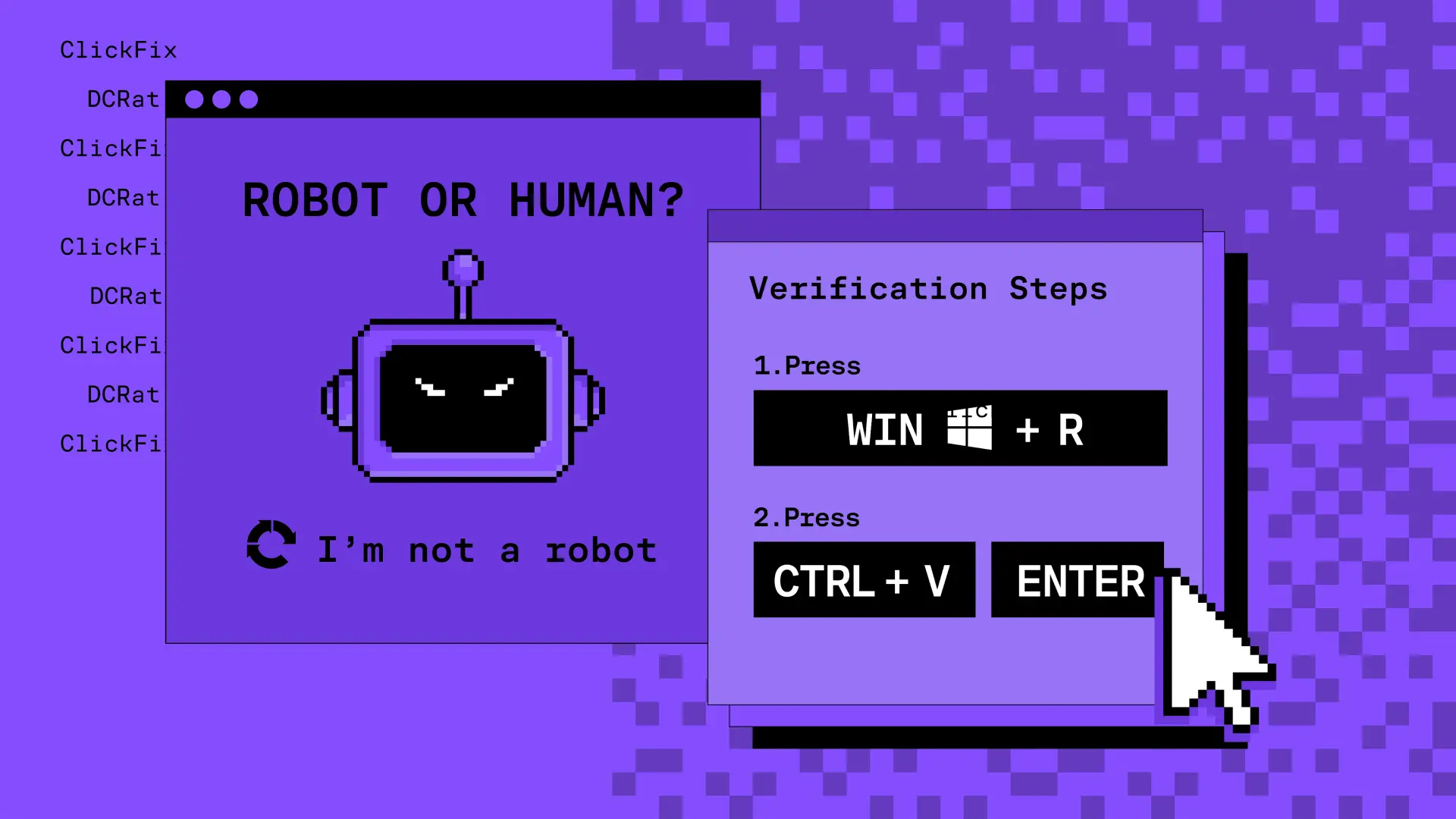
A major theme through the week was the resurgence of fake browser update lures distributed via ClickFix-style malvertising chains.
Users encountered update pop-ups on compromised WordPress and news sites — each mimicking Chrome, Edge, or Firefox update prompts. The payloads delivered modified .msi or .js files that, once executed, installed RedLine Stealer or a newly catalogued Go-based loader linked to the “CleanInstall” campaign.
Unlike earlier versions, these pop-ups were asynchronous injections that triggered only after several minutes of page activity, indicating behavioral triggers rather than static embeds. This made automated scanning harder and improved delivery success.
Why it matters:
The blending of ad-network compromise and deferred pop-up delivery shows the continuing sophistication of malvertising ecosystems — one of the few infection methods that bypass email and corporate security layers.
Recommendations:
- Restrict JavaScript execution from third-party ad domains via browser policies.
- Educate staff to distrust any in-browser “update” prompts and use official vendor URLs.
- Leverage DNS-level content filtering for known ad network compromise lists.
2. Supply-Chain Exposure: Compromised Open-Source Packages
Security telemetry indicated multiple npm and PyPI packages updated with embedded credential harvesters between 19–22 October.
While most were quickly removed, the campaign reflects a sustained trend: low-effort dependency compromise for downstream infection.
Analysts traced one incident to an npm package impersonating express-logger2, used by several small backend frameworks. The code captured environment variables on import, exfiltrating API keys via webhook.
Defensive note:
The packages had no typosquatted names, suggesting dependency hijacking of abandoned maintainers rather than brand impersonation.
Recommendations:
- Enable package signing and integrity verification in build systems.
- Mirror dependencies internally and vet all third-party updates.
- Rotate API and cloud credentials regularly to mitigate supply-chain breaches.
3. Government & Service Smishing Campaigns
In Australia, Canada, and the UK, users reported new SMS and email lures posing as tax rebate and identity verification notices.
The lures impersonated government agencies and banks, using near-perfect localization and proper grammar — a marked improvement over past attempts. Links resolved to cloned portals hosted on hacked small-business domains rather than cheap shorteners, making the messages harder to detect.
What’s notable:
- Pages dynamically adjusted based on IP to present local branding.
- QR versions of the same scam circulated on community bulletin boards and printed mailers.
- Several victims reported simultaneous voice follow-ups within 24 hours of clicking, a clear sign of hybrid smish-vish coordination.
Mitigation:
- Maintain staff alerts for any government refund or “account re-verification” prompts.
- Encourage verification through official portals rather than SMS links.
- Use network monitoring to flag outbound requests to newly registered
.cfdand.storedomains — both heavily used in this wave.
4. Stealer-as-a-Service (SaaS) Ecosystem Update
RedLine, Lumma, and RisePro continued to dominate the information-stealer landscape, but researchers noted new cooperation between operators.
Indicators suggest shared infrastructure and joint obfuscation services. The common goal: rapid payload iteration to defeat hash-based detection.
New samples of RedLine used encrypted configuration payloads within .png containers hosted on Discord CDN. RisePro introduced data staging via Telegram bots, reducing reliance on static C2s.
Defensive notes:
- Watch for outbound connections to
cdn.discordapp.comand Telegram API endpoints during binary execution. - Apply content-disarm rules for media files containing abnormal entropy patterns.
- Update detection for Go and .NET hybrid loaders seen in late-October submissions.
5. Social Engineering & AI-Enhanced Deception
Attackers are clearly refining trust manipulation as a weapon.
Deepfake voice incidents rose again, especially in internal payment fraud attempts where cloned voices of senior managers authorized urgent wire transfers.
At the same time, LinkedIn fake recruiter campaigns re-emerged — this time impersonating tech and HR roles at cybersecurity vendors themselves, showing that no sector is exempt from impersonation.
Observation:
Generative AI tools make these campaigns scalable, and small-scale operators now have access to deepfake-as-a-service platforms. Expect voice and video cloning to persist as default social-engineering tools rather than novelties.
6. Infrastructure Abuse & C2 Trends
During the week, researchers observed a marked shift to temporary VPS and CDN-based C2 hosting, with lifespans under 24 hours.
Providers abused include Cloudflare Workers, Vercel edge nodes, and even public CI/CD runners.
Malware samples uploaded to open sandboxes showed command servers embedded within .wasm blobs or WebSocket endpoints on CDN layers — a clear effort to hide in legitimate infrastructure.
Recommendations:
- Implement DNS sinkholes for known C2 distribution ranges.
- Review outbound connections for WebSocket traffic to atypical providers.
- Expand behavioral baselines in EDR to capture low-and-slow beaconing.
7. Defender’s Corner
This week highlighted the need for layered visibility and faster patch cycles:
- Review browser configuration policies to suppress external update prompts.
- Strengthen supply-chain auditing for open-source dependencies.
- Deploy SMS filtering and URL rewriting at mobile-gateway layers.
- Improve incident simulation exercises around deepfake and voice-based social engineering.
- Block direct Discord, Telegram, and CDN endpoints used for payload staging.
- Continue to rotate secrets and API tokens after dependency updates.
Week in Summary
The week of 20–26 October 2025 underscored a simple pattern: attackers no longer rely solely on brute-force technical intrusion. Instead, they hijack the very infrastructure of trust — ad networks, cloud services, and open-source supply chains — to deliver payloads in plain sight.
As deception tactics mature and payloads modularize, organizations must respond by improving both visibility and verification.
Automation can help, but awareness and skepticism remain the first line of defense.
Trust is still the weakest link — and attackers are getting better at speaking its language.