
Cyber Hygiene Wrap-Up — The 10 Commandments of Cyber Awareness
The grand finale — ten timeless principles to live by in your digital life. A condensed summary of everything learned throughout Cyber Awareness Month.">

Incident Response 101 (Part 2) — Reporting, Containing, and Learning
From containment to communication, this post dives into the structured side of incident response — what your team should do once a threat has been confirmed.">

Weekly Threat Trends — Week Commencing 20 Oct 2025
Analysis of the week’s dominant cyber threats — from fake browser updates and supply-chain breaches to scam evolutions exploiting trust in government and payment systems.">

Incident Response 101 (Part 1) — What to Do If You Click a Bad Link
Everyone slips up eventually — even professionals. This guide walks you through exactly what to do in the crucial first minutes after clicking a malicious link.But what matters most isn’t the click — it’s what you do ...">
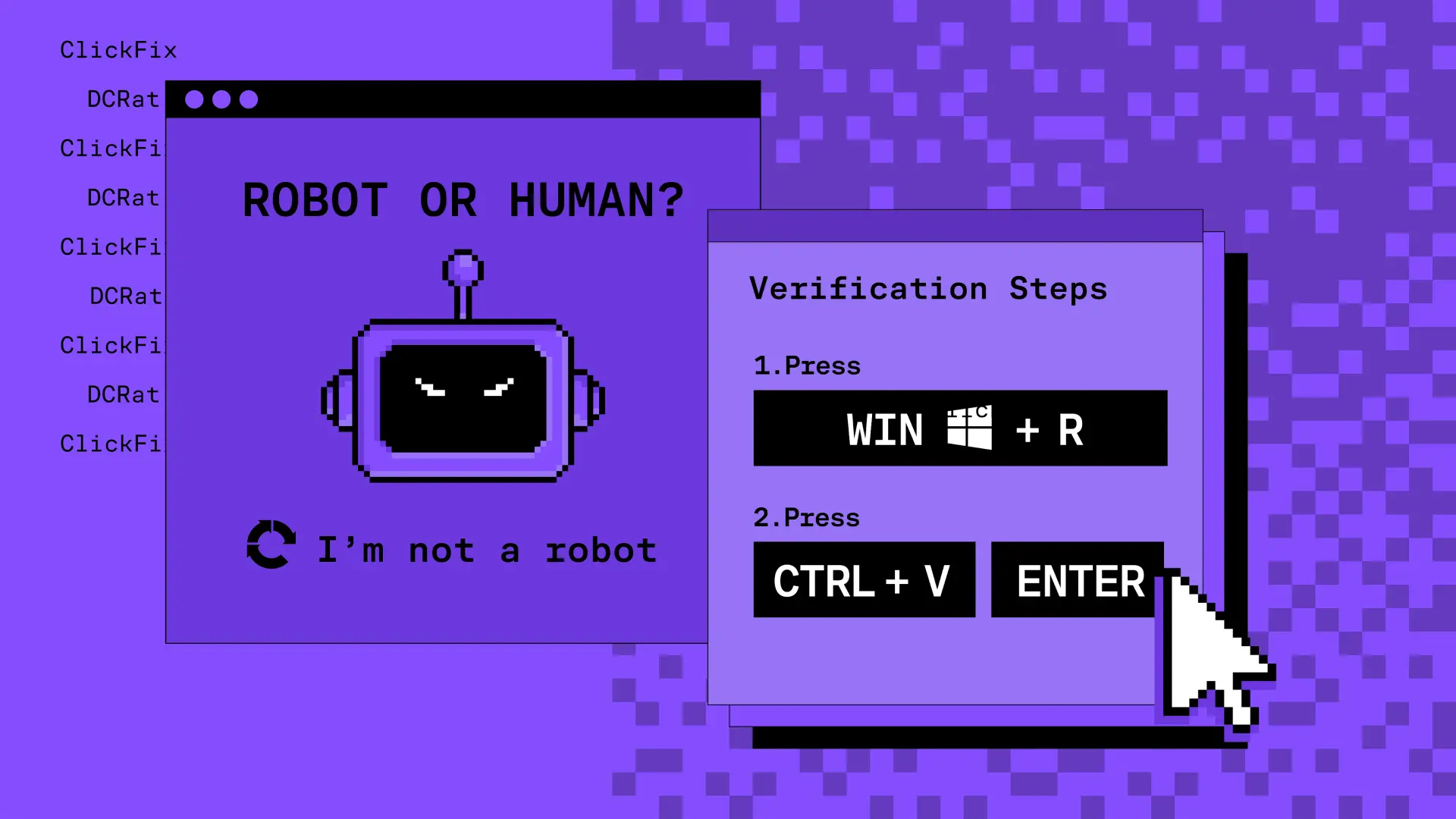
ClickFix Malware Campaign — How Fake Verifications Lead to Real Compromise
A new wave of attacks uses fake 'I'm not a robot' pages and clipboard tricks to make users infect themselves. Here's how it works, what it looks like, and how both users and security teams can respond.">

Home & Personal Security (Part 3) — Protecting Personal Data & App Permissions
Your phone knows more about you than most friends. This awareness piece explores how apps, permissions, and online habits quietly harvest personal data — and what you can do to stop it.">

Current & Trending Threats (Part 2) — QR Phishing, Crypto Scams & SIM Swaps
From QR code bait to SIM swap takeovers and crypto fraud, this post explores three of the most dangerous attack trends dominating 2025 — and how to defend against them.">

When `npm install` Gets You Hacked: The Chollima‑Style Job Scam and How Developers Can Defend Themselves
A deep dive into how attackers weaponize faux 'job challenge' repos and poisoned npm workflows, why developers fall for them, and practical, non‑destructive defenses.">

Weekly Threat Trends — Week Commencing 13 Oct 2025
A detailed look at the cyber threat landscape observed across 13–19 October 2025 — including fake coding interview scams, Salesforce abuse, QR-based phishing, and emerging stealer campaigns.">