Malware
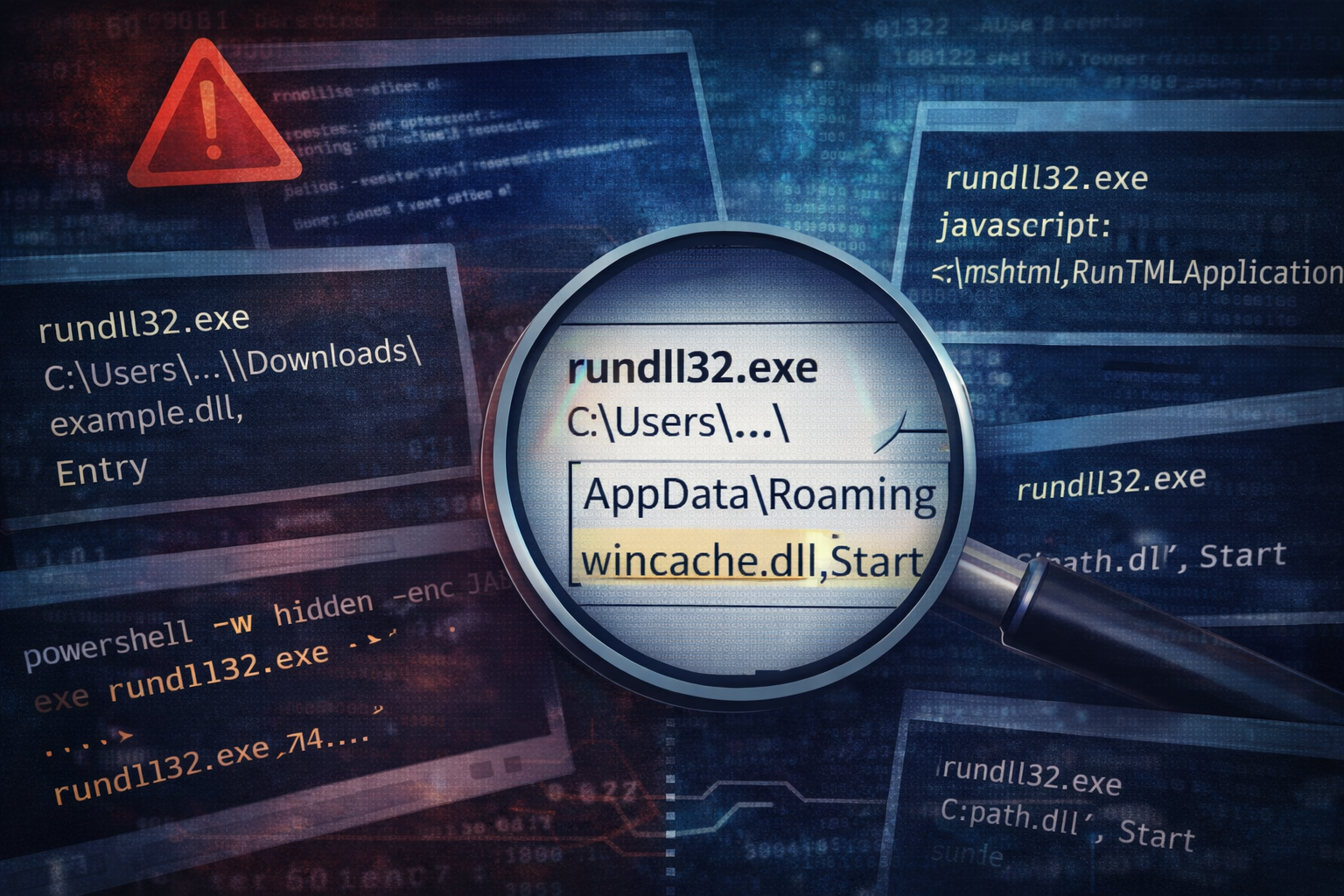
Rundll32 Abuse: The 5 Command Lines I Treat as 'Stop and Look'
rundll32.exe is a legitimate Windows binary, which is exactly why it gets abused. Most rundll32 execution is normal. Some is a gift-wrapped incident waiting to happen. This post lists five high-signal rundll32 command...
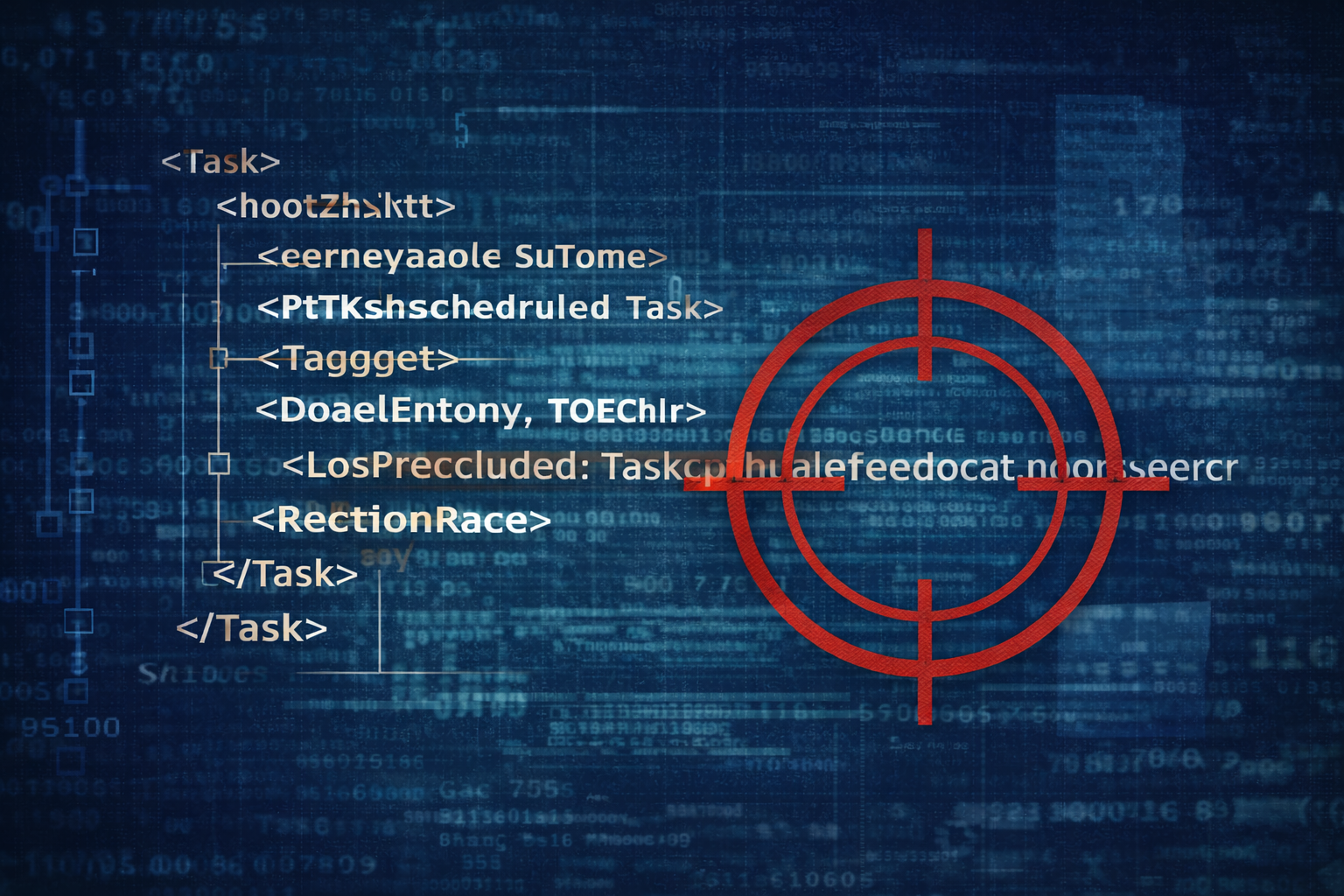
One Artifact: Scheduled Tasks (Why They’re the King of Persistence)
If I had to bet on one persistence mechanism showing up again and again in real incidents, it’s scheduled tasks. They’re reliable, flexible, easy to camouflage, and often under-monitored. This post breaks down how att...

You Have 6 Artifacts—Reconstruct the Kill Chain
No PCAP. No full disk. No luxury. Just six artifacts from endpoint and network telemetry. Your job: reconstruct the kill chain and decide what to do next. In this analyst challenge, I’ll give you the evidence first, t...

Remcos Goes Fileless (Again): Remote Templates, Equation Editor RCE, and .NET-in-Image Loading
FortiGuard Labs documented a 2026 Remcos campaign abusing remote Word templates, CVE-2017-11882, VBScript/WMI execution, and a fileless chain that reflectively loads a .NET module hidden inside an ‘image’—then process...
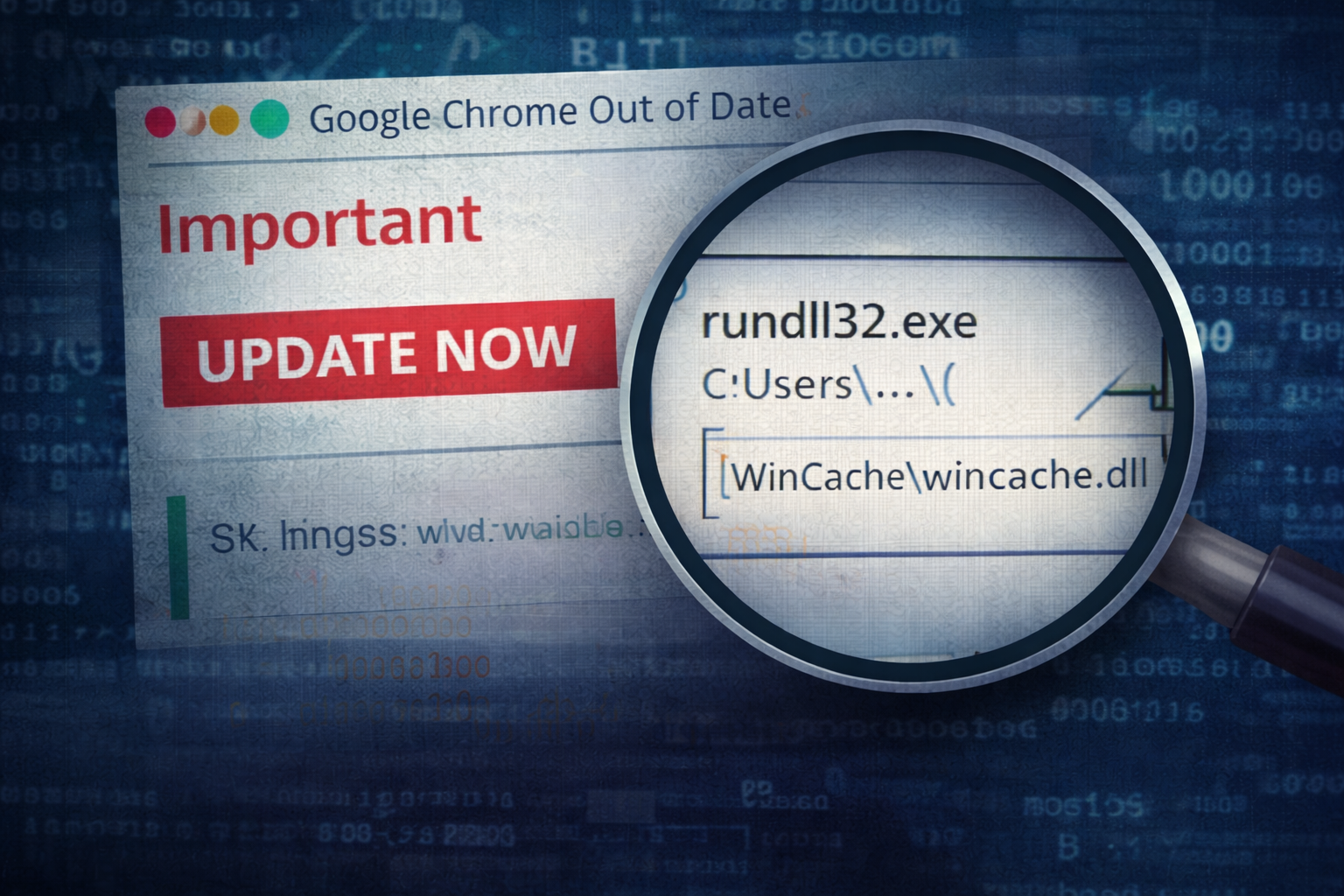
Casefile: The Fake Browser Update That Dropped a Loader
A user clicks what looks like a routine browser update. Within minutes, a ‘legit’ installer chain pivots into rundll32 execution, persistence via scheduled tasks, and outbound beaconing to fresh infrastructure. This c...

Stealer-as-a-Service & the Credential Ecosystem
Infostealers are no longer just one-off binaries dropped by random phishing emails. They are part of a mature Stealer-as-a-Service ecosystem where logs are harvested, packaged, traded, and weaponised for everything fr...

Evasive Loaders & Anti-Analysis Tricks in the Wild
Modern loaders decide if your environment is worth burning a payload on. This post unpacks how they fingerprint sandboxes, abuse LOLBins, and delay execution – and how to flip those anti-analysis tricks into reliable ...

Malware in the Subtitles: A Fake Movie Torrent That Assembles Agent Tesla via Layered PowerShell
A Bitdefender Labs investigation shows a fake movie torrent using a .LNK “launcher” and a subtitle file as a staged script container—decrypting payloads, establishing persistence via Task Scheduler, and ultimately run...

DanaBot Banking Trojan — Back from Operation Endgame
DanaBot is a long-running Windows banking trojan that re-emerged in late 2025 with a rebuilt C2 infrastructure and fresh campaigns. This post walks through how it works, how it’s delivered, and how to investigate and ...

Mispadu Banking Trojan — Latin America’s Credential Harvester
Mispadu is a Latin American–focused banking trojan that blends phishing, malvertising, and social engineering with a modular stealer and remote control back-end. This deep dive walks through how it spreads, how it ope...
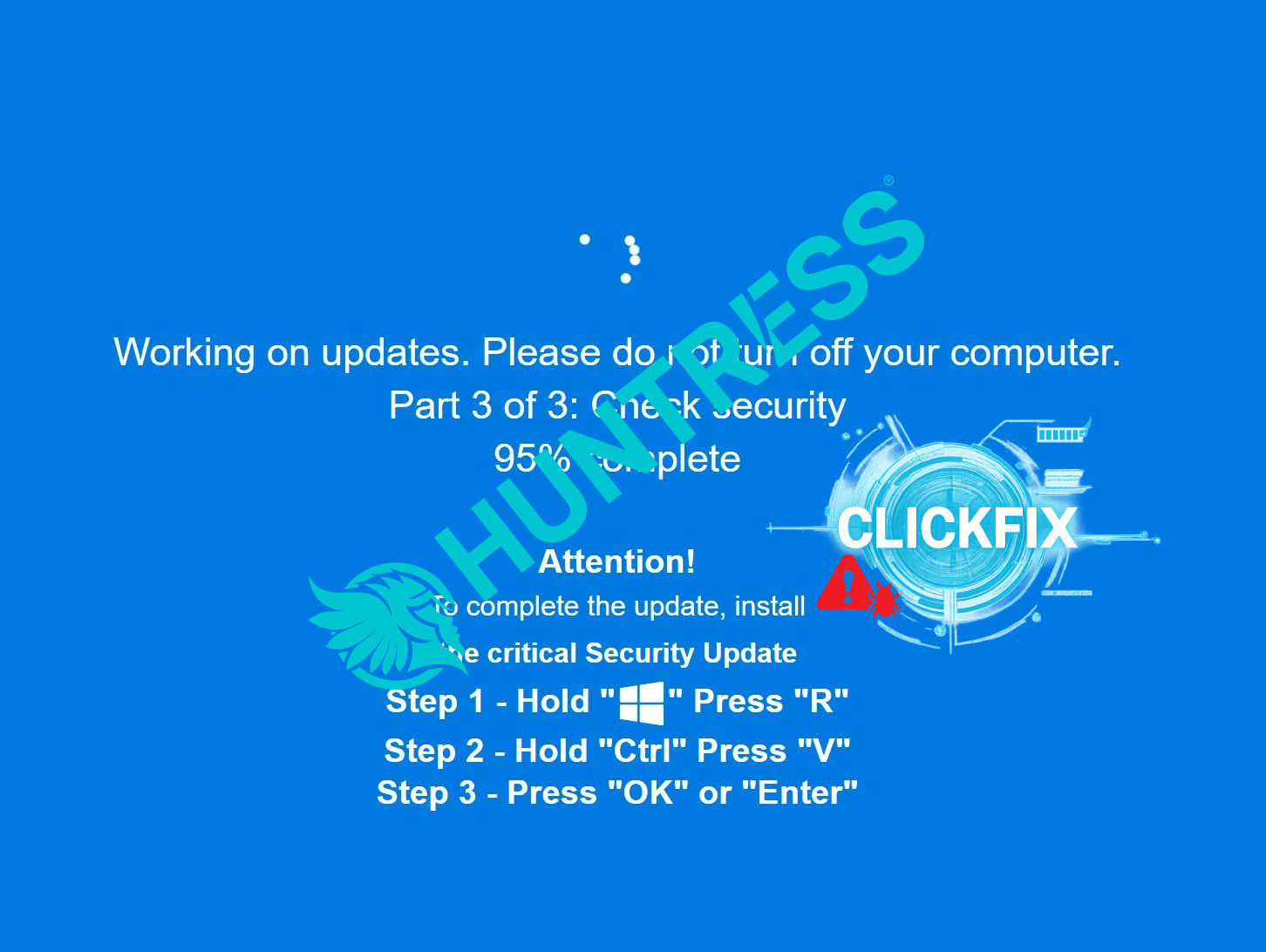
ClickFix Gets Sneaky: Lumma & Rhadamanthys Hiding in PNG Pixels
Notes on a fantastic Huntress write-up by Anna Pham and Ben Folland, walking through a ClickFix campaign where LummaC2 and Rhadamanthys are delivered via steganography inside PNG images.
DarkGate Malware — Loader, Stealer, and RAT in One
DarkGate has quietly evolved into a mature malware-as-a-service platform: loader, stealer, and full-featured RAT. This deep dive breaks down how it spreads, how it operates, and how to hunt it in your environment.

BlackCat (ALPHV) — Ransomware’s Fall and the Clones That Followed
BlackCat (ALPHV) pushed ransomware evolution: polished extortion flows, strong encryption, and a mature affiliate model. This post dissects its internals, TTPs, detection artefacts, and the wave of copycats that follo...

From JSON Keeper to TsunamiKit — Inside the BeaverTail & InvisibleFerret Attack Chain
North Korean threat actors are now abusing fake API keys, JSON Keeper blobs, and GitHub-hosted Node.js projects to deliver a JavaScript loader known as BeaverTail, which drops a Python backdoor (InvisibleFerret) and a...

Rhadamanthys — Modular Malware Done Right (For the Wrong Reasons)
A deep dive into Rhadamanthys, the stealer-loader hybrid redefining modular malware design. We explore its internal architecture, infection vectors, and what defenders can learn from its engineering.
AI-Powered Malware: Dynamic Code Generation and the Rise of Adaptive Threats
A new class of malware is emerging — one that uses AI models to generate, modify, and obfuscate code on demand. This post explores how attackers are weaponizing language models, what this means for detection, and how ...

Lumma Stealer — The Credential Bandit That Won’t Die
Once a low-tier stealer, Lumma evolved into one of 2025’s most persistent credential-harvesting threats. We dissect its infection flow, internal structure, and defense strategies from both blue-team and forensic persp...
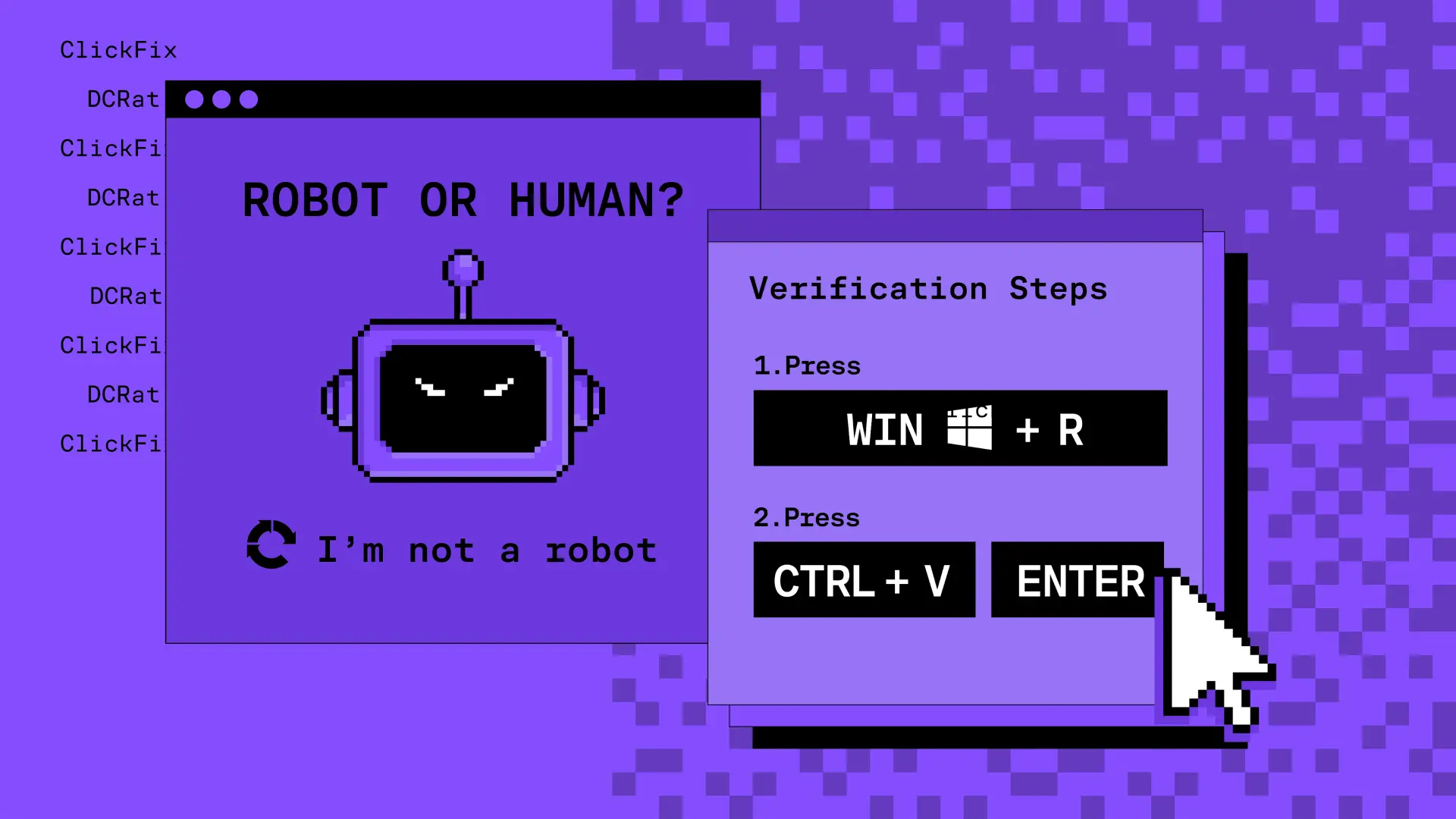
ClickFix Malware Campaign — How Fake Verifications Lead to Real Compromise
A new wave of attacks uses fake 'I'm not a robot' pages and clipboard tricks to make users infect themselves. Here's how it works, what it looks like, and how both users and security teams can respond.

When `npm install` Gets You Hacked: The Chollima‑Style Job Scam and How Developers Can Defend Themselves
A deep dive into how attackers weaponize faux 'job challenge' repos and poisoned npm workflows, why developers fall for them, and practical, non‑destructive defenses.

Malvertising – When Ads Deliver Malware
Malvertising has evolved into one of the most dangerous attack vectors of 2025. This guide traces its origins, explains how poisoned ads work, dissects real campaigns, and provides detailed defense strategies for both...
RaccoonO365: Inside the Global Phishing-as-a-Service Takedown
Microsoft and Cloudflare dismantled RaccoonO365, a $355/month phishing-as-a-service empire that stole 5,000+ Microsoft 365 credentials across 94 countries. This deep dive explains how the service operated, the scale o...

When the Foundation Cracks: Inside the 2025 NPM Supply Chain Attack
A phishing lure, a stolen maintainer account, and 18 poisoned NPM packages: the September 2025 supply chain attack is the most widespread compromise in NPM history. This deep dive explains what NPM is, how dependency ...

Shortcut to Infection: XenoRAT via Malicious .lnk → WSF → Python
A fake invoice lure leads to a shortcut (.lnk) that fetches a WSF, stages dual ZIP archives (me.zip, deb.zip), and launches pythonw.exe from the user’s Contacts directory. Explorer.exe then takes over network comms, c...

Masquerading with “ん”: A clever Unicode trick in Booking.com phishing campaigns
Hiragana 'ん' used in URL paths to evade filters and trick users — plus FakeCaptcha and HijackLoader payloads. In the wild we see FakeCaptcha gates leading to HijackLoader payloads, stitched into refund-lure phishing t...