BLOG INDEX
2026 10 posts
January 10
-
 Scheduled Tasks: The Persistence Mechanism That Never Dies
Scheduled Tasks: The Persistence Mechanism That Never Dies
-
 Weekly Threat Trends — Week Commencing 19th January 2026
Weekly Threat Trends — Week Commencing 19th January 2026
-
 The 6-Artifact Challenge: What Actually Happened Here?
The 6-Artifact Challenge: What Actually Happened Here?
-
 Remcos Goes Fileless: .NET Assemblies Hidden in Images + CVE-2017-11882
Remcos Goes Fileless: .NET Assemblies Hidden in Images + CVE-2017-11882
-
 Weekly Threat Trends — Week Commencing 12th January 2026
Weekly Threat Trends — Week Commencing 12th January 2026
-
 Fake Browser Update → Loader Execution in Minutes
Fake Browser Update → Loader Execution in Minutes
-
 Implementing the ASD Essential Eight: Practical Hardening for Windows & Linux
Implementing the ASD Essential Eight: Practical Hardening for Windows & Linux
-
 Weekly Threat Trends — Week Commencing 5th January 2026
Weekly Threat Trends — Week Commencing 5th January 2026
-
 Initial Access Brokers & Ransomware Chains
Initial Access Brokers & Ransomware Chains
-
 Weekly Threat Trends — Week Commencing 29th December 2025
Weekly Threat Trends — Week Commencing 29th December 2025
2025 63 posts
December 12
-
 Stealer-as-a-Service & the Credential Ecosystem
Stealer-as-a-Service & the Credential Ecosystem
-
 Weekly Threat Trends — Week Commencing 22nd December 2025
Weekly Threat Trends — Week Commencing 22nd December 2025
-
 Evasive Loaders & Anti-Analysis Tricks in the Wild
Evasive Loaders & Anti-Analysis Tricks in the Wild
-
 Weekly Threat Trends — Week Commencing 15th December 2025
Weekly Threat Trends — Week Commencing 15th December 2025
-
 Memory Forensics for Stealers & Loaders
Memory Forensics for Stealers & Loaders
-
 Weekly Threat Trends — Week Commencing 8th December 2025
Weekly Threat Trends — Week Commencing 8th December 2025
-
 Malware in the Subtitles
Malware in the Subtitles
-
 Browser & Credential Artefact Forensics on Windows
Browser & Credential Artefact Forensics on Windows
-
 DanaBot Banking Trojan — Back from Operation Endgame
DanaBot Banking Trojan — Back from Operation Endgame
-
 Weekly Threat Trends — Week Commencing 1st December 2025
Weekly Threat Trends — Week Commencing 1st December 2025
-
 Windows Endpoint Timeline Forensics — Rebuilding the Story from Artefacts
Windows Endpoint Timeline Forensics — Rebuilding the Story from Artefacts
-
 Mispadu Banking Trojan — Latin America’s Credential Harvester
Mispadu Banking Trojan — Latin America’s Credential Harvester
November 15
-
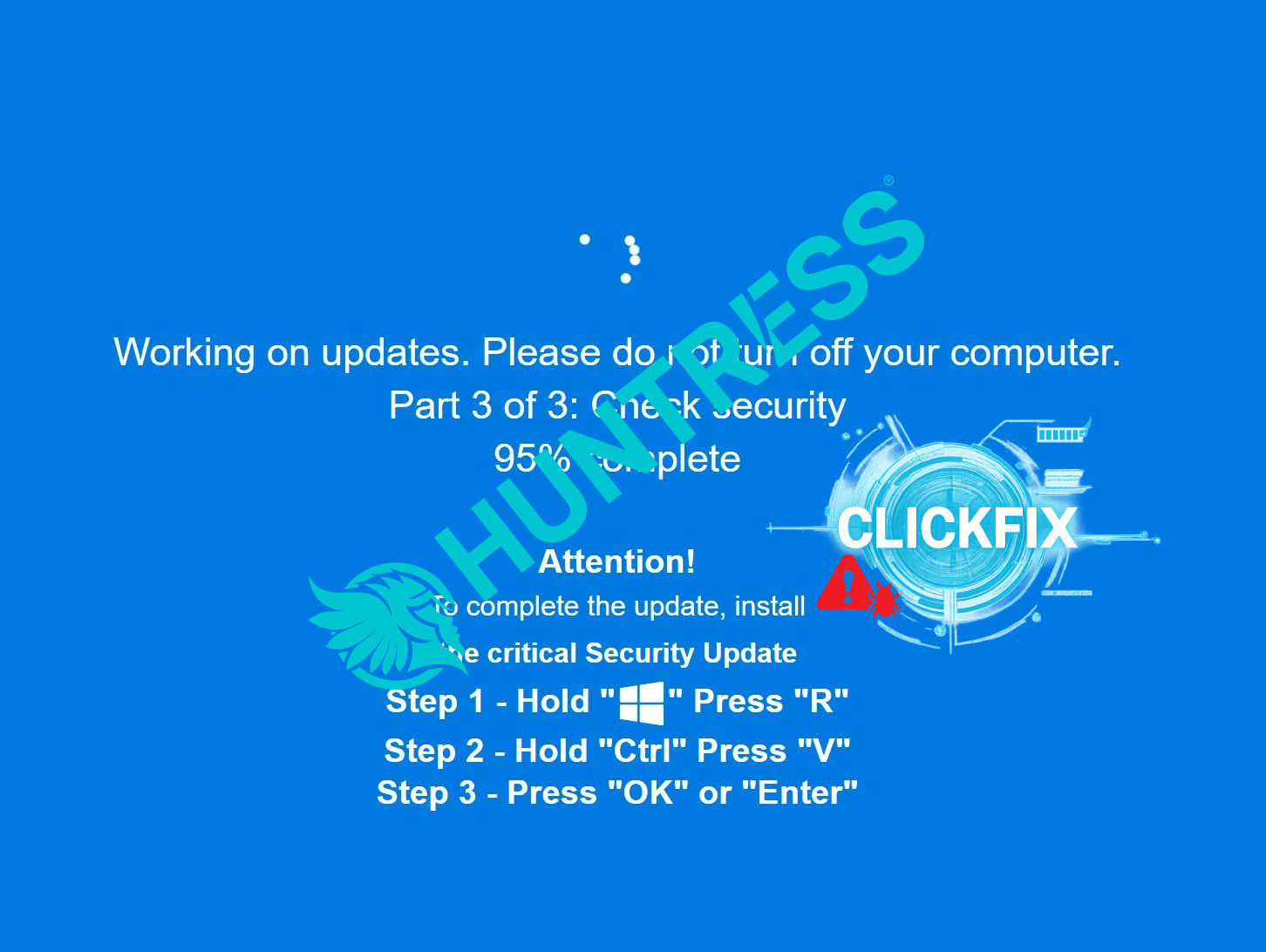 ClickFix Gets Sneaky: Lumma & Rhadamanthys Hiding in PNG Pixels
ClickFix Gets Sneaky: Lumma & Rhadamanthys Hiding in PNG Pixels
-
 Cloud Forensics — Investigating Incidents in AWS, Azure & GCP
Cloud Forensics — Investigating Incidents in AWS, Azure & GCP
-
 DarkGate Malware — Loader, Stealer, and RAT in One
DarkGate Malware — Loader, Stealer, and RAT in One
-
 Weekly Threat Trends
Weekly Threat Trends
Week Commencing 17 Nov 2025 -
 Email Forensics — Tracing a Phish End-to-End
Email Forensics — Tracing a Phish End-to-End
-
 BlackCat (ALPHV) — Ransomware’s Fall and the Clones That Followed
BlackCat (ALPHV) — Ransomware’s Fall and the Clones That Followed
-
 Weekly Threat Trends
Weekly Threat Trends
Week Commencing 10 Nov 2025 -
 From JSON Keeper to TsunamiKit — Inside the BeaverTail & InvisibleFerret Attack Chain
From JSON Keeper to TsunamiKit — Inside the BeaverTail & InvisibleFerret Attack Chain
-
 Network Forensics — Tracking a C2 Through PCAPs
Network Forensics — Tracking a C2 Through PCAPs
-
 Rhadamanthys — Modular Malware Done Right (For the Wrong Reasons)
Rhadamanthys — Modular Malware Done Right (For the Wrong Reasons)
-
 Weekly Threat Trends
Weekly Threat Trends
Week Commencing 3 Nov 2025 -
 AI-Powered Malware:
AI-Powered Malware:
Dynamic Code Generation & the Rise of Adaptive Threats -
 Disk & Memory Forensics 101 — Finding Persistence in the Noise
Disk & Memory Forensics 101 — Finding Persistence in the Noise
-
 Lumma Stealer — The Credential Bandit That Won’t Die
Lumma Stealer — The Credential Bandit That Won’t Die
-
 Weekly Threat Trends
Weekly Threat Trends
Week Commencing 27 Oct 2025
October 19
-
 Cyber Hygiene Wrap-Up
Cyber Hygiene Wrap-Up
The 10 Commandments of Cyber Awareness -
 Incident Response 101 (Part 2)
Incident Response 101 (Part 2)
Reporting, Containing, and Learning -
 Weekly Threat Trends
Weekly Threat Trends
Week Commencing 20 Oct 2025 -
 Incident Response 101 (Part 1)
Incident Response 101 (Part 1)
What to Do If You Click a Bad Link -
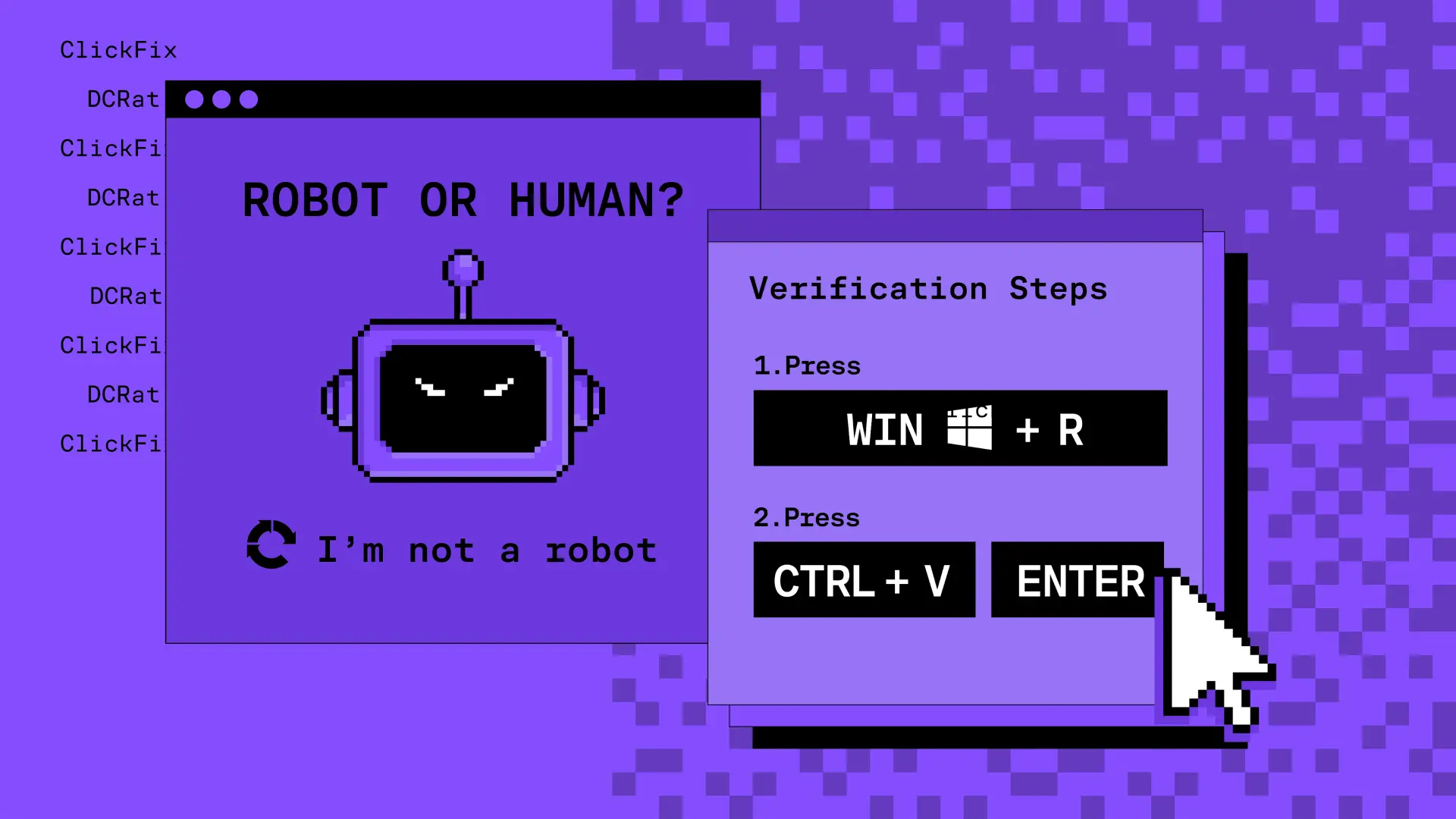 ClickFix Malware Campaign
ClickFix Malware Campaign
How Fake Verifications Lead to Real Compromise -
 Home & Personal Security (Part 3)
Home & Personal Security (Part 3)
Protecting Personal Data & App Permissions -
 Current & Trending Threats (Part 2)
Current & Trending Threats (Part 2)
QR Phishing, Crypto Scams & SIM Swaps -
 When npm install Gets You Hacked
When npm install Gets You Hacked
The Chollima‑Style Job Scam & Developer Defenses -
 Weekly Threat Trends
Weekly Threat Trends
Week Commencing 13 Oct 2025 -
 AI Data Exposure —
AI Data Exposure —
The Human Factor Behind GPT Incidents -
 Home & Personal Security (Part 2)
Home & Personal Security (Part 2)
Teens, Gaming, and Oversharing -
 Salesforce Abuse in Meta Support Phishing
Salesforce Abuse in Meta Support Phishing
How Threat Actors Exploit Trusted Platforms -
 Current & Trending Threats (Part 1)
Current & Trending Threats (Part 1)
AI‑Powered Phishing & Deepfakes -
 Core Cyber Hygiene (Part 2)
Core Cyber Hygiene (Part 2)
Safe Browsing, Email, and Backups -
 Sextortion Scams Are Back
Sextortion Scams Are Back
What They Are, How They Work, and Why They’re So Effective -
 Home & Personal Security (Part 1)
Home & Personal Security (Part 1)
Smart Devices & Home Wi-Fi -
 Core Cyber Hygiene (Part 1)
Core Cyber Hygiene (Part 1)
Passwords, MFA, and Updates -
 OSINT Pt.6: Dating Apps & OSINT
OSINT Pt.6: Dating Apps & OSINT
Risks of Photos, Locations & Bio Info -
 OSINT Pt.5: 5-Minute OSINT
OSINT Pt.5: 5-Minute OSINT
What Strangers Can Learn
September 13
-
 OSINT Pt.4: Following a Scam Trail
OSINT Pt.4: Following a Scam Trail
From Email Headers to Domain Ties -
 Malvertising
Malvertising
When Ads Deliver Malware -
 OSINT Pt.3: Geolocation OSINT
OSINT Pt.3: Geolocation OSINT
Landmarks, Shadows & Weather -
 OSINT Pt.2: Social Media OSINT
OSINT Pt.2: Social Media OSINT
TikTok, Facebook & Instagram -
 RaccoonO365:
RaccoonO365:
Inside the Global Phishing-as-a-Service Takedown -
 OSINT Pt.1: Image OSINT
OSINT Pt.1: Image OSINT
Reverse Image Search, Metadata & Deepfakes -
 When the Foundation Cracks:
When the Foundation Cracks:
Inside the 2025 NPM Supply Chain Attack -
 Branded Phishing
Branded Phishing
[Fake RFP Email] -
 Business Email Compromise
Business Email Compromise
[A Complete Guide] -
 Smishing & Phone Scams
Smishing & Phone Scams
-
 Phishing Awareness
Phishing Awareness
[A Complete Guide] -
 Scam Awareness
Scam Awareness
[A Complete Guide] -
 Shortcut to Infection
Shortcut to Infection
XenoRAT via Malicious .lnk → WSF → Python



